Get certified, let us help!
To pass your certification exam you need the knowledge and the right approach.
We teach you the curriculum, how to study right, and how to approach exam questions.
Get started on you Cyber Security career with the CC certification.
There are RIGHT NOW over 769,000 open Cyber Security jobs in the US, and we are seeing the same trends across the world.
That is almost as many job openings are there are people employed in Cyber Security.
Cyber Security is growing, FAST
There are currently 4.5 million job in Cyber Security and the number of jobs are expected to grow 11-12% annually. That is close to 500,000 new jobs every year.
All of these are included:
- 17.5 hours of CC videos
- 1,700 CC questions in 17 tests
- 60+ chapter CC practice questions
- ThorBot: Your 24/7 AI study assistant, clarify concepts, tailor your learning, and enhance your CC preparation.
- 120 page CC study guide
- A 2,500 CC word Glossary
- 2,500 CC Flashcards
- A CC study plan
- CC Mnemonics
- Subtitles in English, Spanish (Latin America), French, Arabic, Chinese, Japanese and Hindi
- Lifetime or 12-months unlimited access
- 2022 curriculum updated, 2023, and 2024 updated.
To pass your Certified in Cybersecurity (CC) certification you really need 4 things and we will teach you all of them.
- The knowledge; be able to explain the concepts, where/when/why/how we would use it.
- The ability to deconstruct questions to figure out; what are they ACTUALLY asking here?
- The ability to pick the MOST right answer, there may be 2 more or less right answers. Which answer is the MOST right in this specific situation in the eyes of ISC2?
- Time management, you will get 100 questions and you have 2 hours for the exam, meaning you have 72 seconds per question on average.
Your instructor:

Thor Pedersen
CISSP, CISM, CC, PMP, CDPSE, CEH, 2x CCNP, Sec+, 3x CCNA ...
Best selling CISSP, CISM, CC, and PMP trainer with over 580,000 enrollments worldwide.
20+ years experience working with most aspects of IT, information security, project management, and IT training.
Frequently asked CC: Certified in Cybersecurity questions:
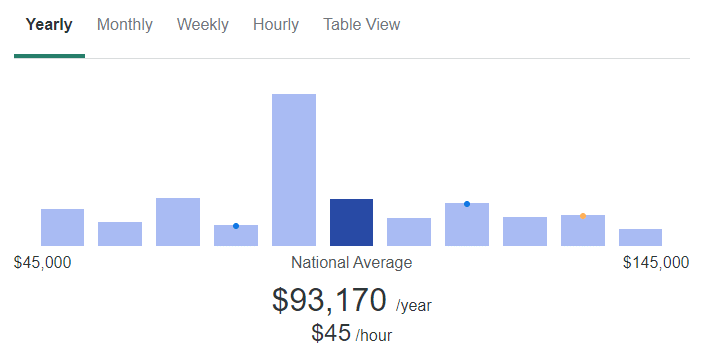
I can’t promise you anything, but there is a huge demand for Cyber Security certified professionals, there are currently 769,000 open Cyber Security jobs in the US alone and we are seeing the same picture across the world.
The average Cyber Security Specialist salary in the US is over $93,000 per year.
https://www.ziprecruiter.com/Salaries/Cyber-Security-Specialist-Salary
You should be able to pass your Certified in Cybersecurity (CC) exam just using my course, IF you use it right.
This is the approach I use for all my studying and it seems to work for the majority of my students.
- Watch the entire course, take notes, use the study guide, and answer the chapter questions.
- Re-watch each video class at 1.5x – 2x speed, take notes.
- Do the full practice tests to find your weak areas, restudy those.
- Rewatch the videos as needed to fill knowledge gaps.
- Keep doing practice tests until you consistently hit 80%+ on all domains.
You need to understand ALL the concepts, be able to explain them, and be able to logic your way through convoluted exam questions.
You need to spend some time learning to deconstruct questions; what are they really asking here?
Do not worry if you spend 2-3 minutes on a question to begin with, just learn to deconstruct the question.
Deconstruct questions and answers:
• Read the question; spot the keywords (PKI, Integrity, HIPAA) and indicators (FIRST, MOST, BEST), then deconstruct the question; what are they really asking here.
• Once you have deconstructed the question, read the answer options.
• Deconstruct the answer options too if needed.
It is possible for questions have 2 distractors and 2 possible right answers.
After each practice test, review the questions you got wrong, read the question explanation. Then re-study your notes, the study guides, and re-watch the video topics you answered wrong on the test.
Re-study the topic until you understand WHY the right answer is the right answer, and why you answered it wrong.
All this is included in our courses:
17.5 hours of Certified in Cybersecurity (CC) videos
1,700 Certified in Cybersecurity (CC) practice questions (in 17 tests)
60+ chapter Certified in Cybersecurity (CC) practice questions
Subtitles in English, Spanish (Latin America), French, Arabic, Chinese, Japanese and Hindi
A 2,500 word Glossary
2,500 Flashcards
120+ pages Certified in Cybersecurity (CC) study guides – (for all 5 domains)
A Certified in Cybersecurity (CC) study plan
200+ Certified in Cybersecurity (CC) links
Yes!
We made our Certified in Cybersecurity (CC) study guides using our slides, you get over 120+ pages of Certified in Cybersecurity (CC) study guides when you purchase our full CC course.
Yes!
You have unlimited access for either Lifetime or 12 months, you can watch the videos and answer the questions as many times as you want.
The Certified in Cybersecurity (CC) exam is linear, meaning once you have answered a question, you can’t go back.
You get 100 questions and you have 2 hours to answer them, meaning on average 72 seconds per question,
There are no prerequisites, this certification has no experience requirements.
There are 5 domains on the ISC2 Certified in Cybersecurity (CC) exam
Domain 1:Security Principles making up 26% of the exam questions.
Domain 2: Business Continuity (BC), Disaster Recovery (DR) & Incident Response Concepts – making up 10% of the exam questions.
Domain 3: Access Controls Concepts – making up 22% of the exam questions.
Domain 4: Network Security – making up 24% of the exam questions.
Domain 5: Security Operations – making up 18% of the exam questions.
Certified in Cybersecurity (CC) certification holders are required to earn 45 CPEs per 3-year cycle, pay a $50 Annual Maintenance Fee (AMF) and adhere to ISC2’s Code of Ethics.