Types of attackers:
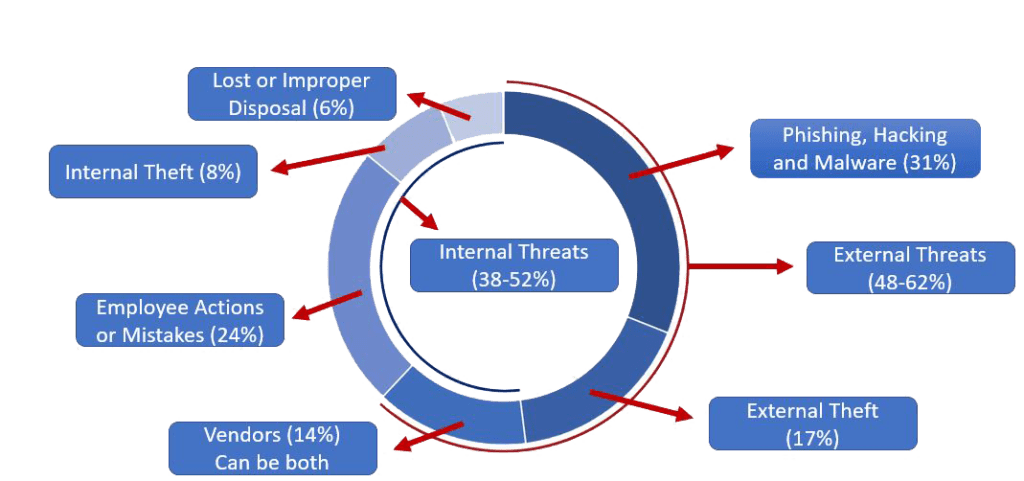
- Outsiders:
- Unauthorized individuals – Trying to gain access, they launch the majority of attacks, but are often mitigated if the organization has good Defense in Depth.
- Interception, malicious code (e.g., virus, logic bomb, Trojan horse), sale of personal information, system bugs, system intrusion, system sabotage or unauthorized system access.
- 48-62% of Risks are from outsiders.
- Insiders:
- Authorized individuals – Not necessarily to the compromised system, who intentionally or unintentionally compromise the system or data.
- This could be: Assault on an employee, blackmail, browsing of proprietary information, computer abuse, fraud and theft, information bribery, input of falsified or corrupted data.
- 38-52% of Risks are from insiders, another reason good Authentication and Authorization controls are needed.


