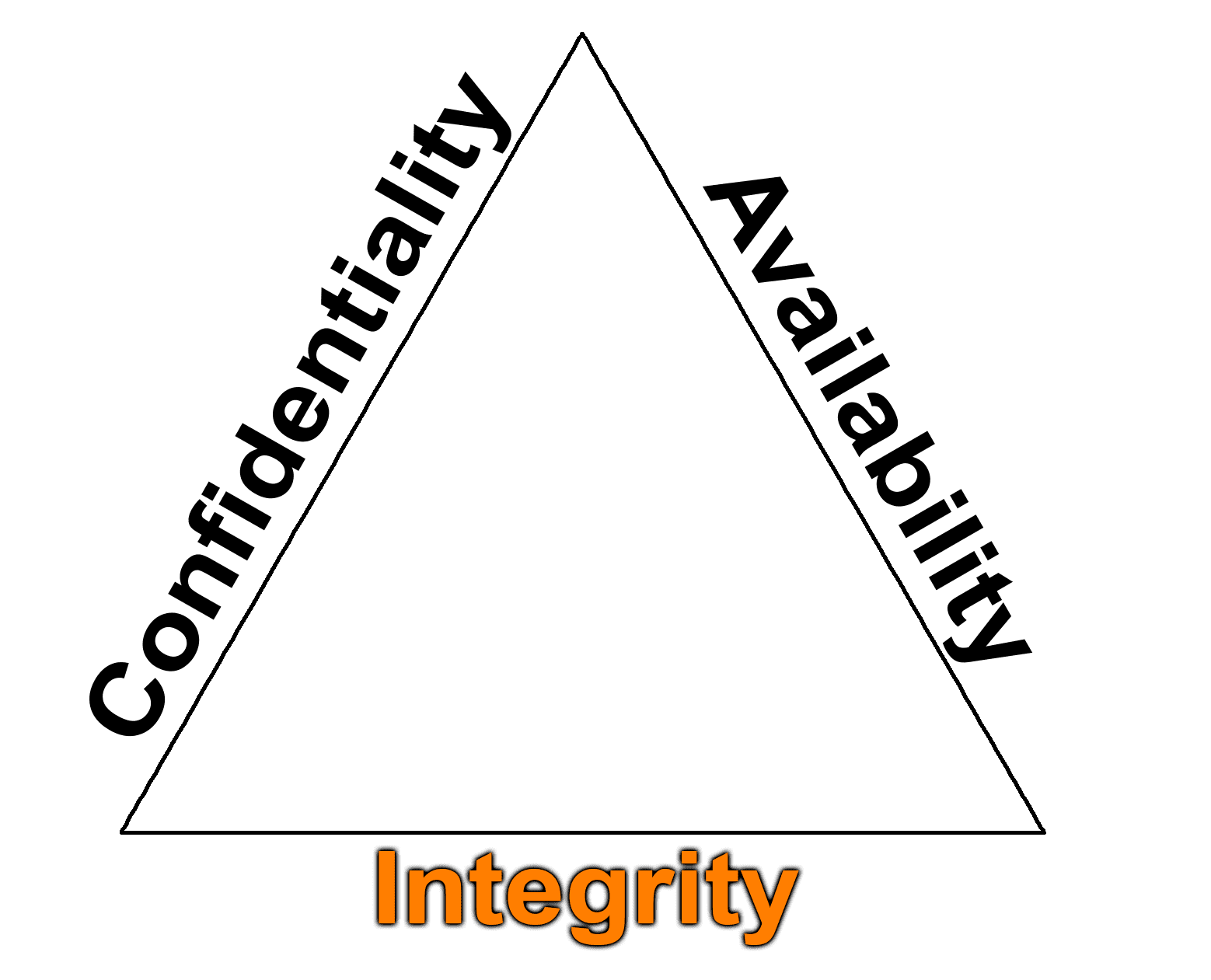
- We want system and Data integrity
- We use:
- Cryptography (again).
- Check sums (This could be CRC).
- Message Digests also known as a hash (This could be MD5, SHA1 or SHA2).
- Digital Signatures – non-repudiation.
- Access control.
- Threats:
- Alterations of our data.
- Code injections.
- Attacks on your encryption (cryptanalysis).
- We use: