Updates we are working on 💻 🗓️
- An updated CISSP course for the 2024 exam.
- Flashcards for 2,500 IT, Business, and Cybersecurity terms.
- A completely new CCSP course ETA TBD.
- A course on using generative AI for Project Management.
Updates we have completed 🍾 🎯 🎊
Video and test courses updates:
Our FREE “CISSP: How to study course” – Get it here.
Our CC (Certified in Cybersecurity) course was updated in 2022, 2023, and will get more updates in 2024 – Get it here.
Our CISM course was updated in 2022, 2023, and we plan 2024 updates – Get it here.
All courses:
We have added subtitles in English, Spanish (Latin America), French, Arabic, Chinese, and Hindi to all our CISSP, CISM, and CC courses.
Practice question updates:
CC (Certified in Cybersecurity): Get them here
Added 1,700 new questions.
CISSP: Get them here
Added 3,250 new Easy/Mid CISSP questions – both as exam emulation and per-domain tests.
Added 125 new Hard CISSP questions.
Added 198 new CISSP topic quizzes added to our CISSP videos after each major topic.
Other:
150+ student names added to our practice questions, we want you to be part of our questions.
Glossary updates:
Our FREE 2,500 word IT and Cybersecurity Glossary – CISSP, CISM, CC, CCSP:
https://thorteaches.com/glossary/
ThorBots (Chatbots) updates:
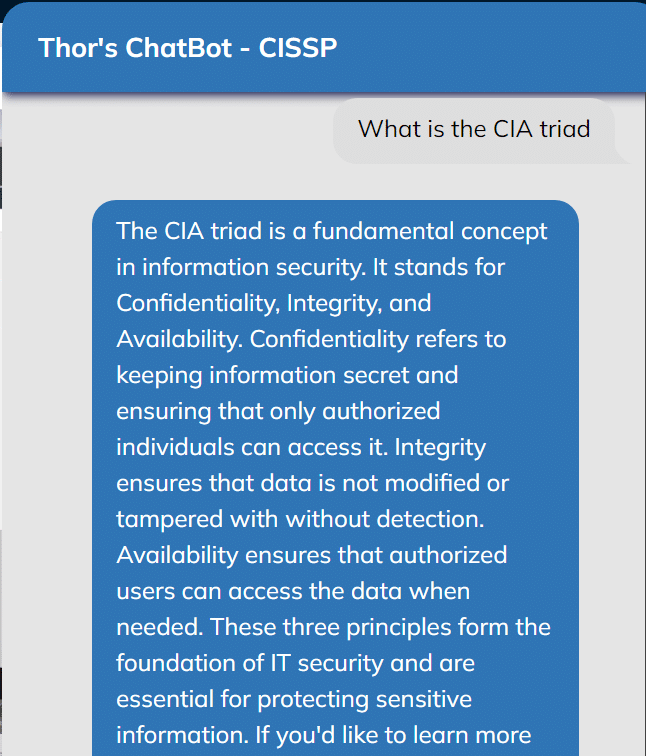
ThorBot:
Your 24/7 AI study assistant, clarify concepts, tailor your learning, and enhance your CISSP, CISM, and CC preparation. The ThorBots are included in our CISSP, CISM, and CC courses here on ThorTeaches.com
Indexes for acceability updates:
Added page indexes to all our Study Guides and Quick Sheets for better accessibility and navigation.
The NEW Thor's CISSP Quick Sheets:

Introducing the NEW “Thor’s CISSP Quick Sheets”.
Streamline your review sessions, maximize your retention!
We know you're busy, and that's why we've distilled our comprehensive CISSP Study Guides down to the essentials.
ThorTeaches.com proudly presents our new CISSP Quick Sheets – the ultimate condensed study notes tailored for your review sessions.
We have already added the CISSP Quick Sheets to our courses on Udemy and ThorTeaches.com, there is no additional charge or price increase, just another awesome study resource to help you succeed.
You can download them from the resources section in the first or second lecture of the course.
Our CISSP 2021 course (being updated before the April 15th 2024 exam change – Get it here.
Our FREE “CISSP: How to study course” – Get it here.
Our CC 2022 (Certified in Cybersecurity) course – Get it here.
Our CISM 2022 curriculum updates – Get it here. <- next update is in 2027
All courses:
Added subtitles in English, Spanish (Latin America), French, Arabic, Chinese, and Hindi to all our CISSP, CISM, and CC courses.
Practice question updates:
CC (Certified in Cybersecurity): Get them here
Added 1,700 new questions.
CISSP: Get them here
Added 3,250 new Easy/Mid CISSP questions – both as exam emulation and per-domain tests.
Added 125 new Hard CISSP questions.
Added 198 new CISSP topic quizzes added to our CISSP videos after each major topic.
Other:
150+ student names added to our practice questions, we want you to be part of our questions.
Yes, there will be detailed explanations of why the correct answer is correct and why the incorrect answers are incorrect.
Easy (E) level sample question:
Louise is the IT security manager for a large financial institution. She has recently implemented a new access control system that utilizes multi-factor authentication for all employees to access sensitive data. One of her employees, Hanna, has reported that she is unable to access certain data that she should have access to. After investigating the issue, Louise discovered that Hanna's access privileges were inadvertently revoked by another employee. What is the most appropriate action to take in this situation?
- Reassign Hanna's access privileges to the appropriate level.
- Have Hanna go through the multi-factor authentication process again to verify her identity.
- Have Hanna go through the entire onboarding process again, including security training and background checks.
- Terminate Hanna's employment for security breaches.
The correct answer:
Reassign Hanna's access privileges to the appropriate level: This is the most reasonable and efficient solution. The issue at hand is that Hanna's access privileges were mistakenly revoked. The most direct way to resolve the problem is to reassign these privileges at the level that is appropriate for her role. This should allow Hanna to access the data she needs for his work. We might also want to investigate how it happened to see if we want to implement further checks to avoid this in the future.
The incorrect answers:
Have Hanna go through the multi-factor authentication process again to verify her identity: The issue isn't with Hanna's identity verification but rather with her access privileges. Re-doing the multi-factor authentication won't restore access to the resources she needs.
Have Hanna go through the entire onboarding process again, including security training and background checks. This approach is unnecessary and time-consuming. The issue doesn't stem from Hanna's actions or a lack of training. It's a mistake in the access control settings. Also, making an employee repeat the onboarding process because of a simple administrative error could lead to frustration and lower morale.
Terminate Hanna's employment for security breaches: This is inappropriate because Hanna didn't commit any security breaches. In fact, she reported the problem. Her access was revoked due to an internal administrative error, not because of her own actions. Taking such a drastic step as termination would not only be unjust, but it could also create a hostile environment where employees may be afraid to report problems in the future.
All of them will be on ThorTeaches.com; most will be on Udemy.
CC Udemy has 1,200 CC questions, ThorTeaches.com has all 1,700 questions.
The CISSP courses on Udemy has 2,500 Easy/Mid questions as exam emulation and 1,000 as per-domain questions.
ThorTeaches.com has 3,250 Easy/Mid questions as exam emulation and 3,250 as per-domain questions.
Both have 625 HARD CISSP questions.
For UB (Udemy Business) students, you should have access to the new Udemy tests as soon as they are added to UB.
All the E/M tests are being retired and replaced with newer and better tests. all this is done in place, so your courses get updated for free. Hard questions are being added to.
On Udemy, we are updating questions in the current tests. We are also making new courses on Udemy for all the other questions.
On ThorTeaches.com, we are adding all the new questions to the bundles there; if you are a current subscriber, you get them all for free.
We plan to raise our prices to match all the new content, but we will announce a 1-week period where you can buy the bundle at the old price but still get all the new questions for free.
They will be better formulated with much better explanations. The test interface stays the same on Udemy and ThorTeaches.com.
Yes, all questions are based on the current CC (2023), CISSP (2021), and CCSP (2022) exams, and they will be updated when the exams change again.
The CISSP exam, will update April 15th. 2024, CCSP 2025, CC 2026, and CISM 2027. Questions will be updated at that time.
It's the same place you do now; we are just updating the back-end practice tests.
A ton of student requests, “Why don’t you have more questions?”, “Can you make more questions, please?”, “I really want just to use your questions,” and many more.
You ask, I listen 😊
Yes, please! With that many new questions, your feedback is invaluable to us.
Aamir, Abhishek, Abiola, Abwino, Adeel, Adu, Ala, Alamgeer, Alfred, Alpesh, Alvin, Amolak, André, Andreas, Ashish, Ashlyn, Brent, Chinthake, Chirayu, Claire, Daniel, Debashish, Dhievy, Donita, Edward, Emmanuelle, Erin, Esther, Evan, Fahim, Garry, Gireesha, Guru, Gurudev, Habib, Hannah, Hind, Hrishikesh, Ishara, Ismail, Ivan, Ivy, Jacob, Jai, Javed, Jay, Jeyapaul, Joe, Joy, Joye, KaTina, Kazim., Khoa, Kobamelo, Kojo, Krzysztof, Kundai, Kushal, Leny, Livaniel, Liz, Malini, Marc, Marius, Maston, Melissa, Mervin, Michael, Moshood, Moxi, Nader, Neeraj, Newton, Olatunde, Omar, Philip, Pierre, Prasanth, Raghavendran, Rami, Ravi, Ritesh, Riz, Robert, Rogelio, Rohit, Ron, Ryan, Saad, Saeed, Sajeevkumar, Sameer, Sartsatat, Serena, Seth, Stuart, Syed, Tai, Taye, Terence, Tewfik, Thilina, Travis, Tristan, Tunde, Vihanga, Vikas, Vinit, Yokesh, Zaw, Scott, Jason, Prashant, Marteen, Fadi, Luc, Shon, Ku'uipo, Chris, Kaimana, Sara, Yasmine, Maria, Melissa, Fatma, Fatima, Nora, Mariam, Emma, Olivia, Isabella, Victoria, Ana Maria, Carmen, Helena, Manuela, Guadalupe, Malu, Esther, Kyra, Sofía, Luna, Zahra, Himari, Latifa, Shu-fen, Amelia, Freja, Agnes, Lív, Ronja, Louise, Hanna, Kamilė, Zuzanna, Anastasia, Astrid, Amelia, Leilani, Kalea, Makana, Kamalani, Francesca, Juanita, Prabh, Ana,Henry, Mikey, Syed, Ushakiran, Sanjay, Paskorn, Suobo, Darwin, Adeel, Jose
Our FREE 2,500 word IT and Cybersecurity Glossary – CISSP, CISM, CC, CCSP: https://thorteaches.com/glossary/

ThorBot:
Your 24/7 AI study assistant, clarify concepts, tailor your learning, and enhance your CISSP, CISM, and CC preparation. The ThorBots are included in our CISSP, CISM, and CC courses here on ThorTeaches.com
ThorBot FAQ:
-
What are the ThorTeaches Chatbots?
Our AI Chatbots are digital study assistants that support interactive learning, offer on-demand assistance, and provide smart study strategies for CISSP, CISM, and Certified in Cybersecurity (CC) certifications.
-
How do I access the chatbots?
The chatbots are available exclusively for ThorTeaches.com students. Just log in to your account, and you'll find them ready to assist you.
-
Can anyone use the chatbots?
While full access is reserved for our students, we offer a free version with limited features on our website for everyone to try.
-
What kind of materials are the chatbots trained on?
The chatbots are trained using our video courses, study guides, mnemonics, NIST documents, Wikipedia articles, ISC2 and ISACA websites, our own "How to Study" materials, and various study guides like The CISSP Process Guide, The Sunflower Notes, and The Memory Palace.
-
Can the chatbots help me understand complex topics?
Yes, you can ask them to explain complicated subjects in simpler terms to enhance your understanding.
-
Are the chatbots available 24/7?
Absolutely! Our chatbots are ready to provide assistance around the clock, any day of the week.
-
Will the chatbots provide personalized study tips?
They sure can. The chatbots will offer tailored advice based on our proven study methods and resources.
-
Can I rely on the chatbots for accurate information?
While the chatbots are trained to provide accurate information, please be aware that they may occasionally make errors. Always cross-reference with authoritative sources when in doubt.
-
Do the chatbots offer support for exam logistics and scheduling?
Yes, they can provide information on exam rules, registration, and scheduling processes.
-
What is the cost of using the chatbots?
The chatbots are included as part of the educational resources provided to students of ThorTeaches.com. The slimmed-down version on our website is free.
-
How do the chatbots handle copyrighted content?
Our chatbots are trained on non-copyrighted, copyright with attribution, or proprietary ThorTeaches materials.
-
Can the chatbots help with mnemonic devices?
Yes, they can teach you mnemonics to improve your memory of important concepts.
-
Can the chatbots help with mnemonic devices?
Yes, they can teach you mnemonics to improve your memory of important concepts.
-
Is there a limit to the number of questions I can ask the chatbots?
No, you can ask unlimited questions and engage with the chatbots as much as you need.
-
Are the chatbots updated regularly?
Yes, we ensure our chatbots are updated in line with the latest information and best practices.
-
Do the chatbots cover all domains of the certification exams?
Yes, they provide assistance across all domains covered in the CISSP, CISM, and CC exams.
-
Will the chatbots replace my need for traditional study methods?
No, they act as a complement to traditional methods by providing interactive and dynamic learning assistance.
-
Can the chatbots help me prioritize my study topics?
Yes, ask the chatbot for advice on which topics to focus on based on your knowledge gaps and exam weightings.
Added page indexes to all our Study Guides and Quick Sheets for better accessability.

Added page indexes to all our Study Guides and Quick Sheets for better accessibility and navigation.

Introducing the NEW “Thor’s CISSP Quick Sheets”.
Streamline your review sessions, maximize your retention!
We know you're busy, and that's why we've distilled our comprehensive CISSP Study Guides down to the essentials.
ThorTeaches.com proudly presents our new CISSP Quick Sheets – the ultimate condensed study notes tailored for your review sessions.
We have already added the CISSP Quick Sheets to our courses on Udemy and ThorTeaches.com, there is no additional charge or price increase, just another awesome study resource to help you succeed.
You can download them from the resources section in the first or second lecture of the course.