CISSP (Certified Information Systems Security Professional)
| Content | ||
|---|---|---|
| 34 hours of CISSP videos | ||
| 3,250 Easy/Mid CISSP questions (exam emulation tests) | ||
| 3,250 Easy/Mid CISSP questions (per-domain tests) | ||
| 625 Hard CISSP questions | ||
| 240 Domain practice questions (30 after each domain) | ||
| 198 topic questions after each major topic | ||
| 290-page CISSP Study Guides | ||
| 114-page Quick Sheets | ||
| 2,500 CISSP Flashcards | ||
| A 2,500-word CISSP Glossary | ||
| ThorBot: Your 24/7 AI study assistant, clarify concepts, tailor your learning, and enhance your CISSP preparation. | ||
| Bundle with everything | ||
| CISSP Mnemonics | ||
| Offline video viewing | ||
| Subtitles in English, Spanish (Latin America), French, Arabic, Chinese, and Hindi | ||
| A CISSP study plan | ||
| Updated for the 2024 curriculum. | ||
| (Optional +$70) 700 Boson practice questions. | ||
| Access duration | ||
| Content |
CISM (Certified Information Security Manager)
| Content | ||
|---|---|---|
| 32+ hours of CISM videos | ||
| 150 CISM questions | ||
| 200-page CISM Study Guides | ||
| 2,500 CISM Flashcards | ||
| A 2,500-word CISM Glossary | ||
| ThorBot: Your 24/7 AI study assistant, clarify concepts, tailor your learning, and enhance your CISM preparation. | ||
| Bundle with everything | ||
| CISM Mnemonics | ||
| Offline video viewing | ||
| Subtitles in English, Spanish (Latin America), French, Arabic, Chinese, and Hindi | ||
| A CISM study plan | ||
| 2022 curriculum updated, 2023, and 2024 updated. | ||
| Access duration | ||
| Content |
CC (Certified in Cybersecurity)
| Content | ||
|---|---|---|
| 17+ hours of CC (Certified in Cybersecurity) videos | ||
| 1,700 CC exam emulation questions | ||
| 60+ topic questions after each major topic | ||
| 120-page CC Study Guides | ||
| 2,500 CC Flashcards | ||
| A 2,500-word CC Glossary | ||
| ThorBot: Your 24/7 AI study assistant, clarify concepts, tailor your learning, and enhance your CC preparation. | ||
| Bundle with everything | ||
| CC Mnemonics | ||
| Offline video viewing | ||
| Subtitles in English, Spanish (Latin America), French, Arabic, Chinese, and Hindi | ||
| A CC study plan | ||
| 2022 curriculum updated, 2023, and 2024 updated. | ||
| Access duration | ||
| Content |
CISSP D3 Preview | Digital signatures
Digital signatures can help us with the authenticity, integrity, confidentiality, and non-repudiation of digital messages or documents.
In this video, I cover digital signatures, what they are, how they work, and where we use them, all at the level you need for the CISSP exam.
Learn how Digital Signatures provide integrity and non-repudiation and everything that comes with it.
Plus, exam tips to help you pass your CISSP certification!
Remember, the CISSP exam is a management-level exam, you need the right point of view to pass the exam.
https://youtu.be/p91oGWwUea4
You can get all my courses, free study materials, my free CISSP course and much more on https://thorteaches.com/
Transcript:
In this lecture, we are going to talk about digital signatures and PKI– Public Key Infrastructure. In PKI, we can use both symmetric and asymmetric encryption as well as hashing, and we use that to provide and manage digital certificates, just like we do with asymmetric encryption, we keep our private key secret.
But for PKI, we also store a copy of the key pair somewhere secure.
And that is a key repository, because what if I just kept my private key on my computer and the computer was stolen?
Even if we have full disk encryption, they can’t get you the key, that is nice, but my key is still gone.
Which means that any of the messages that were sent using my public key, I can no longer open because my private key is gone.
So to make sure we can still access the data that we need, regardless if the key is destroyed or lost, we have a key repository.
I have worked in a couple of places where for one reason or another, I needed a new desktop.
After I got the desktop, I would contact the department that handled our digital signatures.
We had the right policies in place on how and when you can retrieve them.
I think in our organization at the time, the request had to come from someone that was a senior director or higher and someone that was in your reporting structure.
They say, yes, Thor is getting a new PC and he needs his private key.
Then we would have two security administrators access the key repository and find my key.
And we had two because it is a dual control.
That means that no single security administrator can access the key repository and retrieve keys that they should not.
Having that dual control significantly reduces the chance of someone doing something malicious.
And I say reduce because it does not remove.
It is just much less likely that two security administrators are both in agreement on doing something wrong. It’s the same dual control you see in movies, when on the spaceship, they have to turn the key at the same time to stop the self-destruct or to start it.
To make sure that Bob, who just lost all his space money in a poker game, doesn’t get angry
and destroy the space station, we have that dual control.
Even if you use digital signatures just for private use, make sure you have a copy of your secret key stored somewhere secure.
And that last part is important, secure.
The attackers will always look for the weak implementation.
So you need to make sure it is not there.
A Key Escrow is similar to our own key repository.
It is a backup of our key pairs that is kept somewhere, but it is kept by our third party and most often it is kept at the request of law enforcement.
Let’s say for whatever reason, our organization is under investigation by some branch of law enforcement.
They can then demand we put our keys in key escrow.
So in six months we can’t say, oh no, we can’t open all those emails because we lost the private key.
And I’m sure that key escrow is a real thing because many companies did that.
They chose to lose the private key so they would not incriminate themselves with the proof of their wrongdoings in the emails or on the servers.
Now, let’s take a look at how a digital signature works and the actual flow of the data.
Over here on the right, you can kind of see a flow.
I am sending an email to Bob and remember, digital signatures give us integrity and non repudiation.
We can add confidentiality to that.
But the way it is most commonly used, it is only integrity and non repudiation.
I send my email to Bob, that is the data packets you see here.
Then I have a hashing algorithm that provides a hash of the data.
I then encrypt that with my private key and that gives us the digital signature along with the data.
I send that over the Internet, Bob receives it, he then uses my public key to decrypt it, then he uses the same hashing algorithm and those two hashes from the algorithm and the one I sent, they have to match.
If they do, we have message integrity.
And since Bob decrypted this with my public key, then that proves that message came from me.
That provides us now repudiation.
We have talked about we can technically add confidentiality to this as well, although it is not very common.
The way we would do this is after I have encrypted the message with my private key, I would then encrypt it again using Bob’s public key.
Since he should be the only person that has his private key, he is the only one that can decrypt my email.
So as you can see on the flow here, we used to hashing for integrity.
Then we use the private and public key for non repudiation and in some cases confidentiality.
Then we send it over the Internet.
Here we mainly use symmetric encryption.
And then Bob again uses the hashing and the asymmetric.
And I have had students that ask me, “Thor do I really need to understand this flow?”
And my default answer is, every time, if I teach it to you, then yes, it is possible to see it on the exam.”
Now, that doesn’t mean you will see it on the exam.
I have no clue.
The question databank for the actual exam is huge.
You may or may not see something on the flow until digital signatures, but why take that chance?
This flow, I think is pretty simple and I have said it before.
The exam is not going to give you definition questions.
You may get something where they might describe the flow of a digital signature and knowing that you can then pick the right answer.
Or they might say we want integrity, non repudiation and confidentiality.
And then the four answer options will give you a flow saying encrypt with Thor’s private key, then encrypt with Bob’s public key.
Then they might say private key, public key, then hash it, then send it.
And if you don’t completely understand the flow, then how can you answer what we should do to get integrity, non repudiation and confidentiality?
Or they might just want integrity and non repudiation.
Well then it is a regular digital signature.
Most of the questions on your exam, you’re going to have to use logic, figure out what are they really asking, and with that knowledge, find the most right answer or the least wrong.
Now, let’s finish this lecture by looking at digital certificates.
Digital certificates are public keys signed with a digital signature.
They can either be client based or server based.
If they are server based, that can be SSL or TLS.
It is assigned to a specific server and stored on the server.
If it is client based, well, then it is your digital signature.
It is assigned to you and stored on your PC.
Since we already covered your digital signature, let’s look at the server based ones, for SSL and certificates, we will most likely use a public CA– Certification Authority.
And that could be someone like GoDaddy or VeriSign, regardless if it is a public or something we have internally in our company, the CA’s job is to issue and revoke certificates.
Then we have an ORA– Organizational Registration Authorities, and that is something we have within our organization.
It authenticates a user or a system and then it issues a certificate.
On top of issuing the certificates, it also looks at which ones have expired and would have been compromised.
And for that it uses a certification revocation list.
Let’s say one of our server certificate has been compromised.
Well, then the ORA revokes that certificate.
Or if an employee leaves our organization, we keep the certificate to make sure that we can decrypt messages.
But we retired from active use.
I have had some students that suggested that we should delete the certificate when they leave the organization.
And no, first off, we need to be able to read their emails.
And what if in six months we get a court order saying we suspect the employee that left you has been part of insider trading, you have ten days to provide us with all the emails from this time period.
So, yeah, we keep the certificates after they leave.
Up till some years ago for SSL and TLS certificates, we did the same thing.
Now we have moved to an online certification status protocol, which is a client server hybrid, and that is OCSP– Online Certification Status Protocol.
Before we will check every single certificate to see if it was expired with the new version we just checked is this specific certificate expired.
And that, of course, is much, much faster.
And the certification and revocation is an ongoing process.
The list is never static, which is also why it makes so much more sense to use that server client hybrid instead of having to go back every time and check.
And while we’re on this topic, let’s take a real quick look at the Clipper chip.
The Clipper chip was a chipset that was developed and promoted by the US NSA.
And what they said was the intention behind it was an encryption deviceto secure data and voice messages, but somehow they were also smart enough to leave built in back doors so they can listen in on all our conversations.
So the intent was that this little chip would be embedded in every device to secure us.
And while it might have secured some things, obviously the main purpose was for them to listen in.
So luckily when they published this, there was a huge public outcry.
It was seen as a huge invasion of privacy, which we now know it was, and that made them pull the plug on it, which was very, very lucky, because after the fact, we discovered a bunch of security holes in the Clipper chip that would have made many more people able to listen in and see everything that you did, not just the NSA.
Many of the security flaws that the Clipper chip had came from the Skipjack cipher, a cipher that was never secure.
And with that, we are done with this lecture.
I will see you in the next one.
CISSP D3 Preview | Attacks on our Cryptography – Part 2
There are a wide variety of ways attackers can try to gain access to our data.
One of the easiest and non-technical approaches is social engineering.
Why waste your time trying to break into a system if you can convince someone to let you in.
In this video, I cover how we can use and prevent social engineering and some common attacks on our cryptography at the level you need for the CISSP exam.
Remember, the CISSP exam is a management-level exam, you need the right point of view to pass the exam.
https://youtu.be/bbtDEWs-m5w
You can get all my courses, free study materials, my free CISSP course and much more on https://thorteaches.com/
Transcript:
In this lecture, we are going to continue with cryptographic attacks.
We just talked about how it is easier to steal the key than it is to break it, but it is even easier if you convince someone to give you the key.
Social engineering can be tremendously successful.
People want to be helpful.
People want to be nice.
They don’t like conflict and they don’t want to get in trouble.
So if you call and say you are from helpdesk, “Hey, this is Thor from help desk. We’re seeing some
problems with your user log-in, there’s some irregularities with your log-in, and I just need to confirm that you are actually you. Please give me your password to confirm that you are.
If not, I’m unfortunately going to have to lock your accounts.”
People are used to doing what they are told.
They don’t want to be locked out from their accounts so they can’t do their work and they just want the somewhat friendly guy from helpdesk to go away and leave them alone.
How do you achieve that?
Well, you give whoever is on the phone what they want.
There was a very successful social engineering attack done by penetration testing company.
The company thought that they had been very clear in their training that users should never under anycircumstances share their password.
So the Pen-Test company rented an ice cream truck.
They drove it up in front of the company office.
They had a sign that said free ice cream for anyone in this company.
We want to thank our employees for being so awesome.
So here is a free ice cream.
All you need to do is to prove that you work here by entering your username and password.
Whatever they entered, they will get an approved message and they will get their free ice cream.
In less than half an hour, that Pen-Testing company was able to get over 90% of the employees’usernames and passwords that were at the location on that day.
Once the employees saw someone else in line getting free stuff that they knew well, then they just went over there to get their free ice cream.
It looked legit.
It had the company logo.
It has to be right.
Let’s get our ice cream.
And this is why I keep saying we need the training to raise their awareness.
If they don’t change their behavior, their awareness, well, then the training doesn’t matter.
And luckily, this was a penetration test.
It was not an attack.
But it is a very good example of how easy it is to get people to do what they do, even if they are completely clear that this is sensitive information they’re giving out.
We are going to cover social engineering more later, but just for now, understand how it works.
And then maybe the different approaches to social engineering.
We have authority that is someone that you either trust or you are afraid of, an authority figure tells you to do something.
You are more likely to comply.
Then we have intimidation.
If you don’t do this, then something bad will happen.
We briefly touched on that.
That was the email to the CEO.
If you don’t open this attachment and reply within 24 hours, then we’re going to sue you
for $1 million.
Then we have consensus, that is you following the crowd.
Everybody else was doing it.
That can be fake reviews on a website or some sort of fake social proof.
Well, that looks legit.
I’m going to buy it.
Then we have scarcity.
That is the only five left in stock, act now or lose out forever.
They never only have five in stock.
Then we have urgency.
Do it now or something happens.
That is the 24 hour limit the CEO got from that email.
The intimidation was the threat.
And then finally, we have familiarity.
Here, you and the attacker has some sort of common ground that you can build on.
This Thor from IT support, can you give me your password?
Oh, I see here in our files that you went to this high school.
So did my sister.
Maybe you know Karen from this year, because we have that common ground, we kind of sort of know each other.
It is now much more likely that they will help you.
Now onto rainbow tables, those are the pre compiled lists of plaintext and matching ciphertext made by using different hashing algorithms, millions and millions of pairs.
So if they somehow get my hashed password, that is ThorIsAwesome, and we didn’t use salting and we didn’t use nuances, then they compared that to their list and they now know my password.
Then we have known plaintext attacks.
The attacker has the plaintext that we used for a password.
They also have the ciphertext.
They then use that to try to figure out which encryption key we used.
If they can figure that out, well, then they can decrypt all the other passwords as well.
Chosen plain text is similar to known plaintext, but here, as the name indicates, we are able to choose the plain text.
So not only do we know the plain text, it is also one of our choice.
Which then brings us to Adaptive Chosen Plaintext.
Here we enter a password, we see the new hash value, then we do it again and again and again.
So each round we adapt what we use as the password.
And if there are any implementation flaws or flaws in the actual hashing algorithm, well then this adaptive approach could possibly help us break it.
Finally, on this slide, we have Meet-in-the-Middle attacks, and this is a more specialized type of attack.
Here, the attacker knows parts of the plaintext and the ciphertext, but they need to break multiple ciphers.
If you remember back to Triple DES K1, then the encryption is the same algorithm, but three different keys.
The attacker would break the first key, then start over, then break the second key, then start over and then break the third key.
And with that, we are done with this lecture.
I will see you in the next one.
CISSP D1 Preview | The ISC² Code of Ethics
The (ISC)² code of ethics and the code of ethics of the organization you work for are something you need to know by heart.
For the CISSP exam, the (ISC)² code of ethics is VERY testable.
In the 2021 update of the CISSP curriculum, it has been moved up in priority. It is something you can learn very quickly and it is easy points on your exam; take them. In this video, I cover the (ISC)² code of ethics.
Remember, the CISSP exam is a management-level exam, you need the right point of view to pass the exam.
https://youtu.be/_ZgHvPQnAxk
You can get all my courses, free study materials, my free CISSP course and much more on https://thorteaches.com/
Transcript:
In this lecture, we’re going to talk about ethics.
They are very important both on the exam, for your job and for your career.
As part of that, you need to know, adhere to and understand the (ISC)² Code of Ethics not just as an IT security professional, but also for the exam.
This is very testable and luckily it’s not very long.
These are easy points.
So take them where you can get them.
And also understand these are high level guidelines.
They should not replace your good ethical judgment.
For the exam, I would know both the Preamble and the actual Ethics Canons.
And yes, I am going to read them to you because they are so important.
The preamble is the safety and welfare of society and the common good, duty to our principles and to each other, requires that we adhere to and be seen to adhere to the highest ethical standards of behavior.
Therefore, strict adherence to this code is a condition of certification.
That means before you take the exam, you will be signing the Code of Ethics.
And if you actually break them, it is possible you can have your certification revoked.
So know them, understand them, and adhere to them.
In most cases, if this happens, if you lose your certification, it will tie back to negligence or gross negligence.
And now, let’s look at the 4 Canons.
Protect society, the common good, necessary public trust and confidence, and the infrastructure.
Act honourably, honestly, justly, responsibly, and legally.
Provide diligent and competent services to the principles.
And last, but very much not least, advance and protect the profession.
And as I mentioned, these are testable.
You sign them.
So know the Preamble, know the Canons and understand the sentiment behind them.
For the exam, there are a couple of other ethics standards that I would know.
First off, we have the Ten Commandments from the Computer Ethics Institute.
Most of these are similar in their intent.
The wording is, however, different.
Thou shall not use a computer to harm other people.
Thou shall not interfere with other people’s computer work.
Thou shall not snoop around in other people’s computer files.
Thou shall not use a computer to steal.
Thou shall not use the computer to bear false witness.
Thou shall not copy or use proprietary software which you have not paid for.
Thou shall not use other people’s computer resources without authorization and proper compensation.
Thou shall not appropriate other people’s intellectual output.
Think about the social consequences of programs you’re writing or systems you are designing.
And finally, thou shall always use a computer in a way that ensures consideration and respect for your fellow humans.
On the exam, I don’t think you’re going to get any questions that are specific saying, “What is this commandment or that commandment?”
I would recognize them, but much more important, understand the intent behind them.
It is pretty simple.
Don’t do stuff you’re not allowed to or that is illegal.
Think about the consequences of your actions and act ethically.
And then as the last ethics standards that you might see on the exam, is the IABs Ethics and the Internet.
And this is what they consider unethical behavior:
To gain unauthorized access to resources on the Internet.
Disrupt the intended use of the Internet.
Waste resources; that can be people, capacity, or computers, through actions like destroying the integrity of computer-based information or compromising the privacy of users.
And then finally, for your job as an IT security professional, you obviously need to know the ethics standards of your organization.
Many large organizations have their own code of ethics. Most of them, just like the (ISC)² one, boil down to the very same key elements; do what is right, don’t steal, and be ethical.
Learn these, know these, and understand them.
They are easy points on your exam.
Updates we are working on 💻 🗓️
- A course on using generative AI for Project Management.
Updates we have completed 🍾 🎯
Video and test courses updates:
Our CISSP course is updated for the 2024 exam changes – Get it here.
Our FREE “CISSP: How to study course” – Get it here.
Our CC (Certified in Cybersecurity) course was updated in 2022, 2023, and will get more updates in 2024 – Get it here.
Our CISM course was updated in 2022, 2023, and we plan 2024 updates – Get it here.
All courses:
We have added subtitles in English, Spanish (Latin America), French, Arabic, Chinese, and Hindi to all our CISSP, CISM, and CC courses.
Practice question updates:
CC (Certified in Cybersecurity): Get them here
Added 1,700 new questions.
CISSP: Get them here
Added 3,250 new Easy/Mid CISSP questions – both as exam emulation and per-domain tests.
Added 125 new Hard CISSP questions.
Added 198 new CISSP topic quizzes added to our CISSP videos after each major topic.
Other:
150+ student names added to our practice questions, we want you to be part of our questions.
Glossary updates:
Our FREE 2,500 word IT and Cybersecurity Glossary – CISSP, CISM, CC, CCSP:
https://thorteaches.com/glossary/
ThorBots (Chatbots) updates:
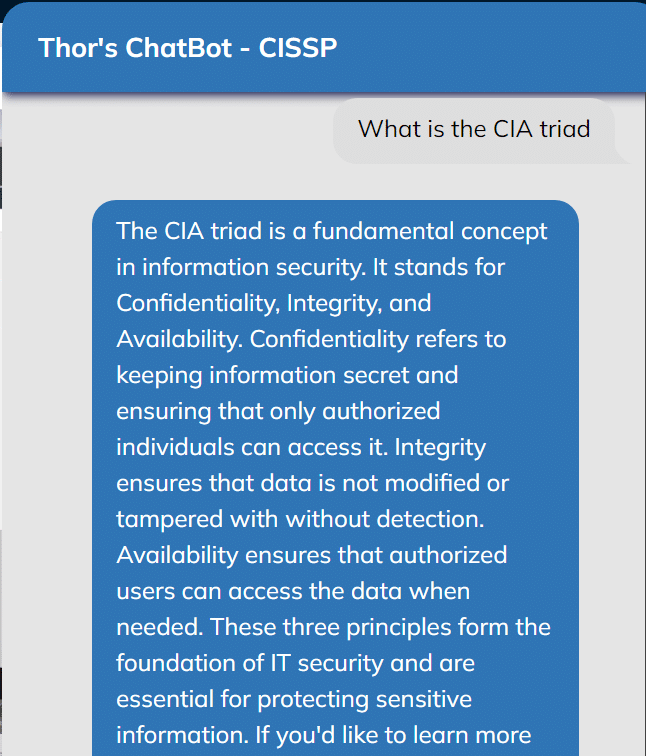
ThorBot:
Your 24/7 AI study assistant, clarify concepts, tailor your learning, and enhance your CISSP, CISM, and CC preparation. The ThorBots are included in our CISSP, CISM, and CC courses here on ThorTeaches.com
Indexes for acceability updates:
Added page indexes to all our Study Guides and Quick Sheets for better accessibility and navigation.
The NEW Thor's CISSP Quick Sheets:

Introducing the NEW “Thor’s CISSP Quick Sheets”.
Streamline your review sessions, maximize your retention!
We know you're busy, and that's why we've distilled our comprehensive CISSP Study Guides down to the essentials.
ThorTeaches.com proudly presents our new CISSP Quick Sheets – the ultimate condensed study notes tailored for your review sessions.
We have already added the CISSP Quick Sheets to our courses on Udemy and ThorTeaches.com, there is no additional charge or price increase, just another awesome study resource to help you succeed.
You can download them from the resources section in the first or second lecture of the course.
Our Flashcards on ThorTeaches.com are LIVE!
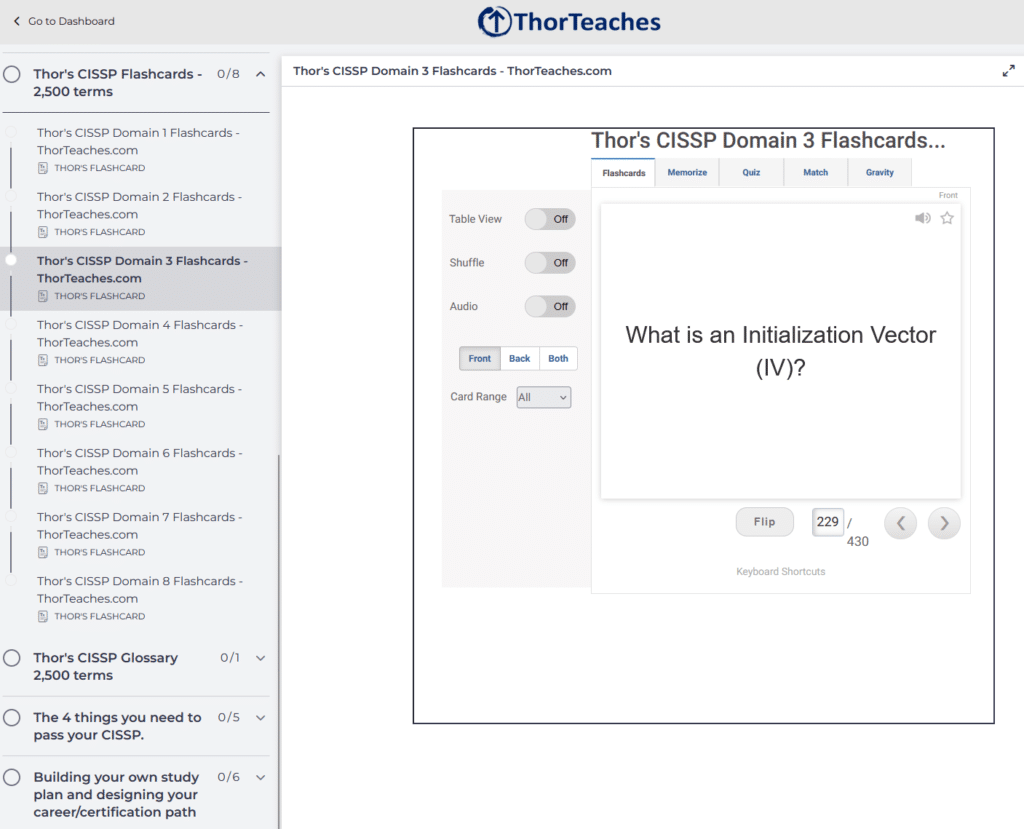
After many many months of working, our 2,500 CISSP, CISM, and CC Flashcards are finally here for you to use.
They are separated into primary domains for each certification as the perfect study aide for self-testing, review sessions, and reinforcing the material covered in our courses.
Where can I get the Flashcards?
They are ONLY available for our students with our CISSP, CISM, and CC courses on ThorTeaches.com, they are not available for Udemy students (sorry but it is an Udemy platform limitation).
Do they cost extra or will you raise your prices?
No, they are part of our full bundles. They were added to all our ThorTeaches.com CISSP, CISM, and CC students courses (right after the domain videos and the Glossary).
Can I use them on mobile devices too?
Yes, they are also accessible on your phone or tablet.
Can I download the flashcards?
No, they are only available on ThorTeaches.com in the courses.
Our CISSP is updated for 2024 exam changes – Get it here.
Our FREE “CISSP: How to study course” – Get it here.
Our CC 2022 (Certified in Cybersecurity) course – Get it here.
Our CISM 2022 curriculum updates – Get it here. <- next update is in 2027
All courses:
Added subtitles in English, Spanish (Latin America), French, Arabic, Chinese, and Hindi to all our CISSP, CISM, and CC courses.
Practice question updates:
CC (Certified in Cybersecurity): Get them here
Added 1,700 new questions.
CISSP: Get them here
Added 3,250 new Easy/Mid CISSP questions – both as exam emulation and per-domain tests.
Added 125 new Hard CISSP questions.
Added 198 new CISSP topic quizzes added to our CISSP videos after each major topic.
Other:
150+ student names added to our practice questions, we want you to be part of our questions.
Yes, there will be detailed explanations of why the correct answer is correct and why the incorrect answers are incorrect.
Easy (E) level sample question:
Louise is the IT security manager for a large financial institution. She has recently implemented a new access control system that utilizes multi-factor authentication for all employees to access sensitive data. One of her employees, Hanna, has reported that she is unable to access certain data that she should have access to. After investigating the issue, Louise discovered that Hanna's access privileges were inadvertently revoked by another employee. What is the most appropriate action to take in this situation?
- Reassign Hanna's access privileges to the appropriate level.
- Have Hanna go through the multi-factor authentication process again to verify her identity.
- Have Hanna go through the entire onboarding process again, including security training and background checks.
- Terminate Hanna's employment for security breaches.
The correct answer:
Reassign Hanna's access privileges to the appropriate level: This is the most reasonable and efficient solution. The issue at hand is that Hanna's access privileges were mistakenly revoked. The most direct way to resolve the problem is to reassign these privileges at the level that is appropriate for her role. This should allow Hanna to access the data she needs for his work. We might also want to investigate how it happened to see if we want to implement further checks to avoid this in the future.
The incorrect answers:
Have Hanna go through the multi-factor authentication process again to verify her identity: The issue isn't with Hanna's identity verification but rather with her access privileges. Re-doing the multi-factor authentication won't restore access to the resources she needs.
Have Hanna go through the entire onboarding process again, including security training and background checks. This approach is unnecessary and time-consuming. The issue doesn't stem from Hanna's actions or a lack of training. It's a mistake in the access control settings. Also, making an employee repeat the onboarding process because of a simple administrative error could lead to frustration and lower morale.
Terminate Hanna's employment for security breaches: This is inappropriate because Hanna didn't commit any security breaches. In fact, she reported the problem. Her access was revoked due to an internal administrative error, not because of her own actions. Taking such a drastic step as termination would not only be unjust, but it could also create a hostile environment where employees may be afraid to report problems in the future.
All of them will be on ThorTeaches.com; most will be on Udemy.
CC Udemy has 1,200 CC questions, ThorTeaches.com has all 1,700 questions.
The CISSP courses on Udemy has 2,500 Easy/Mid questions as exam emulation and 1,000 as per-domain questions.
ThorTeaches.com has 3,250 Easy/Mid questions as exam emulation and 3,250 as per-domain questions.
Both have 625 HARD CISSP questions.
For UB (Udemy Business) students, you should have access to the new Udemy tests as soon as they are added to UB.
All the E/M tests are being retired and replaced with newer and better tests. all this is done in place, so your courses get updated for free. Hard questions are being added to.
On Udemy, we are updating questions in the current tests. We are also making new courses on Udemy for all the other questions.
On ThorTeaches.com, we are adding all the new questions to the bundles there; if you are a current subscriber, you get them all for free.
We plan to raise our prices to match all the new content, but we will announce a 1-week period where you can buy the bundle at the old price but still get all the new questions for free.
They will be better formulated with much better explanations. The test interface stays the same on Udemy and ThorTeaches.com.
Yes, all questions are based on the current CC (2023), CISSP (2021), and CCSP (2022) exams, and they will be updated when the exams change again.
The CISSP exam, will update April 15th. 2024, CCSP 2025, CC 2026, and CISM 2027. Questions will be updated at that time.
It's the same place you do now; we are just updating the back-end practice tests.
A ton of student requests, “Why don’t you have more questions?”, “Can you make more questions, please?”, “I really want just to use your questions,” and many more.
You ask, I listen 😊
Yes, please! With that many new questions, your feedback is invaluable to us.
Aamir, Abhishek, Abiola, Abwino, Adeel, Adu, Ala, Alamgeer, Alfred, Alpesh, Alvin, Amolak, André, Andreas, Ashish, Ashlyn, Brent, Chinthake, Chirayu, Claire, Daniel, Debashish, Dhievy, Donita, Edward, Emmanuelle, Erin, Esther, Evan, Fahim, Garry, Gireesha, Guru, Gurudev, Habib, Hannah, Hind, Hrishikesh, Ishara, Ismail, Ivan, Ivy, Jacob, Jai, Javed, Jay, Jeyapaul, Joe, Joy, Joye, KaTina, Kazim., Khoa, Kobamelo, Kojo, Krzysztof, Kundai, Kushal, Leny, Livaniel, Liz, Malini, Marc, Marius, Maston, Melissa, Mervin, Michael, Moshood, Moxi, Nader, Neeraj, Newton, Olatunde, Omar, Philip, Pierre, Prasanth, Raghavendran, Rami, Ravi, Ritesh, Riz, Robert, Rogelio, Rohit, Ron, Ryan, Saad, Saeed, Sajeevkumar, Sameer, Sartsatat, Serena, Seth, Stuart, Syed, Tai, Taye, Terence, Tewfik, Thilina, Travis, Tristan, Tunde, Vihanga, Vikas, Vinit, Yokesh, Zaw, Scott, Jason, Prashant, Marteen, Fadi, Luc, Shon, Ku'uipo, Chris, Kaimana, Sara, Yasmine, Maria, Melissa, Fatma, Fatima, Nora, Mariam, Emma, Olivia, Isabella, Victoria, Ana Maria, Carmen, Helena, Manuela, Guadalupe, Malu, Esther, Kyra, Sofía, Luna, Zahra, Himari, Latifa, Shu-fen, Amelia, Freja, Agnes, Lív, Ronja, Louise, Hanna, Kamilė, Zuzanna, Anastasia, Astrid, Amelia, Leilani, Kalea, Makana, Kamalani, Francesca, Juanita, Prabh, Ana,Henry, Mikey, Syed, Ushakiran, Sanjay, Paskorn, Suobo, Darwin, Adeel, Jose
Our FREE 2,500 word IT and Cybersecurity Glossary – CISSP, CISM, CC, CCSP: https://thorteaches.com/glossary/
Our Flashcards on ThorTeaches.com are LIVE!
After many many months of working, our 2,500 CISSP, CISM, and CC Flashcards are finally here for you to use.
They are separated into primary domains for each certification as the perfect study aide for self-testing, review sessions, and reinforcing the material covered in our courses.
Where can I get the Flashcards?
They are ONLY available for our students with our CISSP, CISM, and CC courses on ThorTeaches.com, they are not available for Udemy students (sorry but it is an Udemy platform limitation).
Do they cost extra or will you raise your prices?
No, they are part of our full bundles. They were added to all our ThorTeaches.com CISSP, CISM, and CC students courses (right after the domain videos and the Glossary).
Can I use them on mobile devices too?
Yes, they are also accessible on your phone or tablet.
Can I download the flashcards?
No, they are only available on ThorTeaches.com in the courses.

ThorBot:
Your 24/7 AI study assistant, clarify concepts, tailor your learning, and enhance your CISSP, CISM, and CC preparation.
The ThorBots are included in our CISSP, CISM, and CC courses here on ThorTeaches.com.
Updated again Feb 2024 with better back-end (ChatGPT 4-Turbo 128 and better command training.

Added page indexes to all our Study Guides and Quick Sheets for better accessibility and navigation.

Introducing the NEW “Thor’s CISSP Quick Sheets”.
Streamline your review sessions, maximize your retention!
We know you're busy, and that's why we've distilled our comprehensive CISSP Study Guides down to the essentials.
ThorTeaches.com proudly presents our new CISSP Quick Sheets – the ultimate condensed study notes tailored for your review sessions.
We have already added the CISSP Quick Sheets to our courses on Udemy and ThorTeaches.com, there is no additional charge or price increase, just another awesome study resource to help you succeed.
You can download them from the resources section in the first or second lecture of the course.
What are the main practical changes in the CISSP 2024 exam update?
My video on the changes:
https://www.youtube.com/watch?v=nFd0TQ5oBT8
The CISSP 2024 exam update, includes a 1% weight shift from Domain 8 to Domain 1, fewer exam questions (100 to 150 instead of 125 to 175), and a shorter exam duration (3 hours instead of 4). Additionally, there’s an update in curriculum content across various domains, including new and expanded topics.
What are the actual curriculum changes?
Most of the changes is more emphasis on topics that are more relevant and in focus now like cloud computing, AI, privacy, etc.
Domain 1: Added external dependencies in business impact analysis.
Domain 2: No changes we know of.
Domain 3: Added Secure Access Service Edge (SASE), Quantum key distribution, and managing the information system lifecycle.
Domain 4: Added transport architecture, performance metrics, traffic flows, physical segmentations, edge networks, virtual private clouds, and network monitoring and management.
Domain 5: Added services in the control of physical and logical access to assets, policy decision and enforcement points, and service account management.
Domain 6: Emphasis on location context (on-premise, cloud, hybrid) for audit strategies.
Domain 7: Added communication during the testing of Disaster Recovery Plans (DRP).
Domain 8: Added Scaled Agile Framework and software composition analysis.
When will your new content be out for the CISSP changes?
Content for 2024 curriculum changes is now live .
Is anything of the current curriculum getting removed?
We do not think so, as far as we know no curriculum is being removed.
Will there be any new domains introduced in the updated CISSP exam?
No, the eight domains will remain the same; only the content within some domains will be updated or expanded.
How will the question format be affected by the update?
The question format will remain a Computer Adaptive Testing (CAT) format, but with a different number of questions and reduced exam duration.
If I’m already studying, should I attempt the exam before or after the update?
It is generally recommended to take the exam before the update, given that the current materials are available, and you might be more familiar with them. However, if that’s not possible, the changes are considered minor and should not significantly impact your preparation.
Will I need to repurchase your study courses for the updated exam if I already have them?
No, if you have purchased courses from ThorTeaches.com or Udemy, you will receive updates for free. Only the versions on these platforms will be updated.
Can I take the CISSP exam remotely after the update?
No, all exams must be taken in-person at an authorized Pearson-Vue testing center.
What happens if I have already purchased study materials for the current exam but plan to take it after the update?
You should be fine, the changes are very minor. It is advisable to review the new topics from other sources as the update will introduce new content.
When will the new study materials for the 2024 exam changes be available?
For ThorTeaches.com and Udemy courses, updates will be made available before the exam changes. The official study guides, AIO, and practice questions from ISC2 typically become available 3 to 6 months after the exam updates.
Is there going to be a price change for the CISSP exam after the update?
There are no planned changes to the exam pricing.
How can I best prepare for the CISSP exam with the upcoming changes?
It is recommended to continue studying the current materials and familiarize yourself with the new topics. Taking advantage of the free course on how to study for the exam at free.thorteaches.com can provide valuable insights into effective preparation strategies.
Will the format of questions change in the updated CISSP exam?
The format will remain Computer Adaptive Testing (CAT), but there will be a total of 100 to 150 questions instead of the previous range of 125 to 175.
I am scheduled to take the CISSP exam right before the update; will my exam still be valid?
Yes, your exam and assuming you pass and get endorsed, your CISSP certification will be just as valid regardless of whether you take the exam before or after the update.
How much time will I have per question in the updated exam?
If you receive the maximum of 150 questions in your exam, you will have approximately 72 seconds per question within the 3-hour time limit.
What is the passing score for the updated CISSP exam?
The passing score for the CISSP exam remains the same, which is a scaled score of 700 out of 1000 points.
Will there be any changes to the CISSP experience requirements after the update?
There have been no announcements regarding changes to the CISSP experience requirements, which currently entail a minimum of five years of professional security work experience.
Do the CISSP exam updates include changes to the continuing professional education (CPE) requirements?
There are no changes to the CPE requirements for maintaining your CISSP certification.
Will beta questions be included in the updated CISSP exam?
Yes, there will be 25 beta questions randomly dispersed within the first 100 questions of the exam.
Are the beta questions counted towards the final score?
No, beta questions are not counted toward your final score. They are used by ISC2 to validate the questions for future exams.
Will the beta questions be distinguishable from the scored questions?
No, you will not be able to distinguish beta questions from scored questions during the exam.
Can we expect new types of interactive questions in the updated CISSP exam?
There is no specific mention of new question types; the update focuses on content rather than question format.
How will the changes affect the weight of each domain in the CISSP exam?
All domains except for Domain 1 and Domain 8 will maintain their current weights. Domain 1 will increase by 1%, compensated for by a 1% decrease in Domain 8.
Will the difficulty level of the CISSP exam change after the update?
The difficulty is calibrated through the CAT format to reflect a consistent standard of knowledge, so it should remain comparable.
How frequently are the CISSP exam questions updated?
While there is a major curriculum update every three years, the actual exam questions can be updated more frequently to reflect current industry standards and practices.
Will the update affect the application process for the CISSP exam?
The application process for the CISSP exam is not expected to change with the update.
Are there any changes to the CISSP endorsement process after passing the exam?
No changes to the endorsement process have been announced.
Why is Lifetime Access more expensive than the standard 12-month access?
The premium price of Lifetime Access accounts for the ongoing costs to maintain, host, and update the course materials on our platform indefinitely, rather than just for 12 months.
Do I get access to all your courses on ThorTeaches.com when I buy lifetime access?
No, the lifetime access is purchased on a course level. If you want lifetime access to more courses, you need to purchase the courses you want.
Can I upgrade to Lifetime Access on courses I have not purchased?
You can only upgrade courses you own to lifetime access, or you can buy them initially with Lifetime Access.
Will I receive updates to the course with Lifetime Access?
Yes, all in-place updates to the course content are included with Lifetime Access. You’ll automatically receive the most current material without additional charges.
What does Lifetime mean on ThorTeaches.com?
In the context of this policy, “Lifetime” refers to the operational lifetime of the course on our platform, not the lifetime of the individual purchaser. Should ThorTeaches LLC undergo a business transition, such as cessation, sale, or restructuring, you will be provided a download link for the full course and all materials that you are enrolled in, preserving your educational investment. There are no near or long term plans for this, but proper contingencies should be clear.
Are there any maintenance or hidden fees associated with Lifetime Access?
No, there are no maintenance or hidden fees. The one-time premium payment covers all costs associated with the lifetime access to the course materials.
Can I switch from a 12-month access plan to Lifetime Access after my initial purchase?
Yes, you can upgrade to Lifetime Access at any time during your 12-month access period or after it expires. There is no deadline, even if your initial access has expired you can still get lifetime for 45% of the current course list price. It’s more cost-effective to select Lifetime Access at the time of your initial purchase.
Is Lifetime Access transferable to another student or individual?
No, Lifetime Access is non-transferable and is linked exclusively to the account of the original purchaser to ensure the integrity and security of account access.
Does Lifetime Access apply to all courses offered on ThorTeaches.com?
Yes, it is available for all our courses.
Will I still be able to access the course after I finish it?
Absolutely. Once you’ve finish the course, you will retain access to it for as long as your account remains in good standing. That means you can revisit and review the course content whenever you need a refresher or want to retake the entire course.
How often is the course content updated?
We update courses to align with the current exam version, all updates are done in-place. With Lifetime Access, you’re guaranteed to receive all these updates.
Can I get Lifetime Access for the Boson questions?
No, the Lifetime Access is only for our courses, we resell the Boson vouchers, so they are only 12-months access.
Yes, there will be detailed explanations of why the correct answer is correct and why the incorrect answers are incorrect.
Easy (E) level sample question:
Louise is the IT security manager for a large financial institution. She has recently implemented a new access control system that utilizes multi-factor authentication for all employees to access sensitive data. One of her employees, Hanna, has reported that she is unable to access certain data that she should have access to. After investigating the issue, Louise discovered that Hanna's access privileges were inadvertently revoked by another employee. What is the most appropriate action to take in this situation?
- Reassign Hanna's access privileges to the appropriate level.
- Have Hanna go through the multi-factor authentication process again to verify her identity.
- Have Hanna go through the entire onboarding process again, including security training and background checks.
- Terminate Hanna's employment for security breaches.
The correct answer:
Reassign Hanna's access privileges to the appropriate level: This is the most reasonable and efficient solution. The issue at hand is that Hanna's access privileges were mistakenly revoked. The most direct way to resolve the problem is to reassign these privileges at the level that is appropriate for her role. This should allow Hanna to access the data she needs for his work. We might also want to investigate how it happened to see if we want to implement further checks to avoid this in the future.
The incorrect answers:
Have Hanna go through the multi-factor authentication process again to verify her identity: The issue isn't with Hanna's identity verification but rather with her access privileges. Re-doing the multi-factor authentication won't restore access to the resources she needs.
Have Hanna go through the entire onboarding process again, including security training and background checks. This approach is unnecessary and time-consuming. The issue doesn't stem from Hanna's actions or a lack of training. It's a mistake in the access control settings. Also, making an employee repeat the onboarding process because of a simple administrative error could lead to frustration and lower morale.
Terminate Hanna's employment for security breaches: This is inappropriate because Hanna didn't commit any security breaches. In fact, she reported the problem. Her access was revoked due to an internal administrative error, not because of her own actions. Taking such a drastic step as termination would not only be unjust, but it could also create a hostile environment where employees may be afraid to report problems in the future.
All of them will be on ThorTeaches.com; most will be on Udemy.
CC Udemy has 1,200 CC questions, ThorTeaches.com has all 1,700 questions.
The CISSP courses on Udemy has 2,500 Easy/Mid questions as exam emulation and 1,000 as per-domain questions.
ThorTeaches.com has 3,250 Easy/Mid questions as exam emulation and 3,250 as per-domain questions.
Both have 625 HARD CISSP questions.
For UB (Udemy Business) students, you should have access to the new Udemy tests as soon as they are added to UB.
All the E/M tests are being retired and replaced with newer and better tests. all this is done in place, so your courses get updated for free. Hard questions are being added to.
On Udemy, we are updating questions in the current tests. We are also making new courses on Udemy for all the other questions.
On ThorTeaches.com, we are adding all the new questions to the bundles there; if you are a current subscriber, you get them all for free.
We plan to raise our prices to match all the new content, but we will announce a 1-week period where you can buy the bundle at the old price but still get all the new questions for free.
They will be better formulated with much better explanations. The test interface stays the same on Udemy and ThorTeaches.com.
Yes, all questions are based on the current CC (2023), CISSP (2021), and CCSP (2022) exams, and they will be updated when the exams change again.
The CISSP exam, will update April 15th. 2024, CCSP 2025, CC 2026, and CISM 2027. Questions will be updated at that time.
It's the same place you do now; we are just updating the back-end practice tests.
A ton of student requests, “Why don’t you have more questions?”, “Can you make more questions, please?”, “I really want just to use your questions,” and many more.
You ask, I listen 😊
Yes, please! With that many new questions, your feedback is invaluable to us.
Aamir, Abhishek, Abiola, Abwino, Adeel, Adu, Ala, Alamgeer, Alfred, Alpesh, Alvin, Amolak, André, Andreas, Ashish, Ashlyn, Brent, Chinthake, Chirayu, Claire, Daniel, Debashish, Dhievy, Donita, Edward, Emmanuelle, Erin, Esther, Evan, Fahim, Garry, Gireesha, Guru, Gurudev, Habib, Hannah, Hind, Hrishikesh, Ishara, Ismail, Ivan, Ivy, Jacob, Jai, Javed, Jay, Jeyapaul, Joe, Joy, Joye, KaTina, Kazim., Khoa, Kobamelo, Kojo, Krzysztof, Kundai, Kushal, Leny, Livaniel, Liz, Malini, Marc, Marius, Maston, Melissa, Mervin, Michael, Moshood, Moxi, Nader, Neeraj, Newton, Olatunde, Omar, Philip, Pierre, Prasanth, Raghavendran, Rami, Ravi, Ritesh, Riz, Robert, Rogelio, Rohit, Ron, Ryan, Saad, Saeed, Sajeevkumar, Sameer, Sartsatat, Serena, Seth, Stuart, Syed, Tai, Taye, Terence, Tewfik, Thilina, Travis, Tristan, Tunde, Vihanga, Vikas, Vinit, Yokesh, Zaw, Scott, Jason, Prashant, Marteen, Fadi, Luc, Shon, Ku'uipo, Chris, Kaimana, Sara, Yasmine, Maria, Melissa, Fatma, Fatima, Nora, Mariam, Emma, Olivia, Isabella, Victoria, Ana Maria, Carmen, Helena, Manuela, Guadalupe, Malu, Esther, Kyra, Sofía, Luna, Zahra, Himari, Latifa, Shu-fen, Amelia, Freja, Agnes, Lív, Ronja, Louise, Hanna, Kamilė, Zuzanna, Anastasia, Astrid, Amelia, Leilani, Kalea, Makana, Kamalani, Francesca, Juanita, Prabh, Ana,Henry, Mikey, Syed, Ushakiran, Sanjay, Paskorn, Suobo, Darwin, Adeel, Jose
Can I get CPEs/CEUs for finishing your courses?
Yes, when you finish our course you get a Certificate of completion worth 1 CPE per hour of video watched.
You can use them for CPEs with ISACA, CompTIA, ISC2, and many other certification providers.
- The CISSP course is 32 hours long, worth 32 CPEs.
- The CISM course is 32 hours long, worth 32 CPEs.
- The CC (Certified in Cybersecurity) course is 17 hours long, worth 17 CPEs.
What are the ThorTeaches Chatbots?
Our AI Chatbots are digital study assistants that support interactive learning, offer on-demand assistance, and provide smart study strategies for CISSP, CISM, and Certified in Cybersecurity (CC) certifications.
How do I access the chatbots?
The chatbots are available exclusively for ThorTeaches.com students. Just log in to your account, and you'll find them ready to assist you.
Can anyone use the chatbots?
While full access is reserved for our students, we offer a free version with limited features on our website for everyone to try.
What kind of materials are the chatbots trained on?
The chatbots are trained using our video courses, study guides, mnemonics, NIST documents, Wikipedia articles, ISC2 and ISACA websites, our own "How to Study" materials, and various study guides like The CISSP Process Guide, The Sunflower Notes, and The Memory Palace.
Can the chatbots help me understand complex topics?
Yes, you can ask them to explain complicated subjects in simpler terms to enhance your understanding.
Are the chatbots available 24/7?
Absolutely! Our chatbots are ready to provide assistance around the clock, any day of the week.
Will the chatbots provide personalized study tips?
They sure can. The chatbots will offer tailored advice based on our proven study methods and resources.
Can I rely on the chatbots for accurate information?
While the chatbots are trained to provide accurate information, please be aware that they may occasionally make errors. Always cross-reference with authoritative sources when in doubt.
Do the chatbots offer support for exam logistics and scheduling?
Yes, they can provide information on exam rules, registration, and scheduling processes.
What is the cost of using the chatbots?
The chatbots are included as part of the educational resources provided to students of ThorTeaches.com. The slimmed-down version on our website is free.
How do the chatbots handle copyrighted content?
Our chatbots are trained on non-copyrighted, copyright with attribution, or proprietary ThorTeaches materials.
Can the chatbots help with mnemonic devices?
Yes, they can teach you mnemonics to improve your memory of important concepts.
Can the chatbots help with mnemonic devices?
Yes, they can teach you mnemonics to improve your memory of important concepts.
Is there a limit to the number of questions I can ask the chatbots?
No, you can ask unlimited questions and engage with the chatbots as much as you need.
Are the chatbots updated regularly?
Yes, we ensure our chatbots are updated in line with the latest information and best practices.
Do the chatbots cover all domains of the certification exams?
Yes, they provide assistance across all domains covered in the CISSP, CISM, and CC exams.
Will the chatbots replace my need for traditional study methods?
No, they act as a complement to traditional methods by providing interactive and dynamic learning assistance.
Can the chatbots help me prioritize my study topics?
Yes, ask the chatbot for advice on which topics to focus on based on your knowledge gaps and exam weightings.