CISSP (Certified Information Systems Security Professional)
| Content | ||
|---|---|---|
| 34 hours of CISSP videos | ||
| 3,250 Easy/Mid CISSP questions (exam emulation tests) | ||
| 3,250 Easy/Mid CISSP questions (per-domain tests) | ||
| 625 Hard CISSP questions | ||
| 240 Domain practice questions (30 after each domain) | ||
| 198 topic questions after each major topic | ||
| 300+ pages CISSP Study Guides | ||
| 120-page Quick Sheets | ||
| 2,500 CISSP Flashcards | ||
| A 2,500-word CISSP Glossary | ||
| ThorBot: Your 24/7 AI study assistant, clarify concepts, tailor your learning, and enhance your CISSP preparation. | ||
| Bundle with everything | ||
| CISSP Mnemonics | ||
| Offline video viewing | ||
| Subtitles in English, Spanish (Latin America), French, Arabic, Chinese, and Hindi | ||
| A CISSP study plan | ||
| Updated for the 2024 curriculum. | ||
| (Optional +$70) 700 Boson practice questions. | ||
| Access duration | ||
| Content |
CISM (Certified Information Security Manager)
| Content | ||
|---|---|---|
| 32+ hours of CISM videos | ||
| 150 CISM questions | ||
| 200-page CISM Study Guides | ||
| 2,500 CISM Flashcards | ||
| A 2,500-word CISM Glossary | ||
| ThorBot: Your 24/7 AI study assistant, clarify concepts, tailor your learning, and enhance your CISM preparation. | ||
| Bundle with everything | ||
| CISM Mnemonics | ||
| Offline video viewing | ||
| Subtitles in English, Spanish (Latin America), French, Arabic, Chinese, and Hindi | ||
| A CISM study plan | ||
| 2022 curriculum updated, 2023, and 2024 updated. | ||
| Access duration | ||
| Content |
CC (Certified in Cybersecurity)
| Content | ||
|---|---|---|
| 17+ hours of CC (Certified in Cybersecurity) videos | ||
| 1,700 CC exam emulation questions | ||
| 60+ topic questions after each major topic | ||
| 120-page CC Study Guides | ||
| 2,500 CC Flashcards | ||
| A 2,500-word CC Glossary | ||
| ThorBot: Your 24/7 AI study assistant, clarify concepts, tailor your learning, and enhance your CC preparation. | ||
| Bundle with everything | ||
| CC Mnemonics | ||
| Offline video viewing | ||
| Subtitles in English, Spanish (Latin America), French, Arabic, Chinese, and Hindi | ||
| A CC study plan | ||
| 2022 curriculum updated, 2023, and 2024 updated. | ||
| Access duration | ||
| Content |
Get certified, get ahead, with my 96-hour Udemy course sale!

In 2008 I had a choice, certifications or a degree.
I could keep working full time, take care of my wife, and study at night and on weekends.
Within the next 1 1/2 year I got my CCENT, CCNA, CCNP, CEH, CCNA-Security, Security+, and my CISSP.
I started getting interviews without the “required” degree.
Both are obviously better, but if you have to choose one, pick certifications!
CISSP D3 Preview | Mobile device security
Today, there are more mobile devices than people in the world. We connect everything to the internet.
With so many mobile devices, it is critical that we understand where and what they are and that we have the proper protection for all of them.
In this video, I cover those at the level you need for the CISSP exam.
Remember, the CISSP exam is a management-level exam, you need the right point of view to pass the exam.
https://youtu.be/PmgrYBCg5O8
You can get all my courses, free study materials, my free CISSP course and much more on https://thorteaches.com/
Transcript:
In this lecture, we’re going to talk about mobile security and when most people think mobile security, they think cell phones.
But it really is anything you can walk around with, anything we attach, that can be external USB drives, hard drives, tablets, CDs, laptops, anything that is mobile.
And obviously this also covers cell phones.
We have over the last five to eight years, started to add so many more devices to our networks.
And I’m sure this is going to exponentially grow over the next coming years.
The more devices and the more different types of devices we connect, the more complex policies, procedures and standards we need.
We need to ensure that every device we have data on is secure to a point that makes sense for that device and the data.
Most of the internal threats we have is not from malicious people.
They either just don’t know any better or it’s just easier to do it this way.
It’s probably not going to hurt anything.
It’s probably not going to be found out.
So as much as we can, we need to be able to eliminate them, even having the option to try to take the shortcut.
I know of one breach where a guy just wanted to go outside to have a smoke.
He didn’t want to go through the access point, all the control, all that stuff.
It was just much easier to open the back door, go out and smoke and then close the door when he was done, he had been doing it for months.
But one night he forgot to close the door all the way.
He closed it, but he didn’t get that little snap when the lock actually closes, and with that door not being closed, someone was able to get into the building, effectively circumventing all our other security.
He wasn’t malicious.
He wasn’t an intentional, bad actor.
He was just lazy.
Another example that is maybe more appropriate to mobile security was a doctor that compromised Protected Health Information or PHI.
Being the good doctor that he was, he just wanted to check on some patient records and he did not have his laptop with him.
So on his phone, he configured an unsecure mail client.
He checked the patient record he needed and then went on with his day.
A couple weeks later, he did the same thing.
It was easy and he kept doing that.
After some months, the phone was stolen and all that patient information was still on the phone in the mail client.
Again, not a bad guy, just someone who found a loophole and used it because it was easier.
To help with both of these, we obviously need to do the proper training to raise the awareness of our users.
But part of our role is to make sure that those loopholes are closed.
We close the loopholes and then we give them the tools that they need. With the guy that wanted to go out and smoke, he probably just needs to follow protocol.
But with the doctor, what he really needed was a secure male client on his phone.
And then maybe we need to ensure that the phone has full disk encryption and maybe remote wipe capabilities.
For all our mobile devices, we want to ensure that we have the policies, the procedures, and standards in place that we need so we can be as secure as we need to be.
On the technical side of things, we should lock our USB ports down, the CD drives, the network ports are wireless devices, wireless networks and disable auto run on any media that is attached to a laptop or any other portable device.
Wherever it is possible we should have full disk encryption if the device is stolen.
The attacker really has no way of accessing our data and with any device where it is possible that holds sensitive data, we should have some sort of remote wipe capabilities.
Either we send the command to the device and the next time it is online, it wipes itself. Or if it has not been online for 10 or 20 or 30 days, it does a remote wipe on its own.
And yes, there are ways you can circumvent this.
There is anything in IT Security.
That’s not really the point.
The point is we have enough security to protect whatever we are protecting.
Most cell phones already have the remote wipe capability and it is pretty inexpensive to add it to laptops as well.
For this as anywhere else, we want our defense in depth and user training and awareness is a huge part of that.
Cell phones are obviously the most common mobile device we use, and they are also the ones that gets lost the most often, which is probably also lucky, with any current Android or iOS operating system, it will by default have full disk encryption.
I mean, it is possible to turn it off.
But why would you? Now how our employees use their phone if they lose them is something we don’t really have a lot of control over.
If it is their personal phone, all we can do is make sure that they don’t have any confidential or sensitive data on their phones.
What we can do something about is if we issue company phones.
Here, we have a lot more control.
And regardless of which type of phone it is, both private and company phones, we need to ensure that we have the good security standards in place that we need.
And here we are not talking about phones that they only use for private use.
This is phones that is used partially for private use and partially for company use, as well as phones that we have issued.
So for any of the phones that have some sort of company data on it, it doesn’t matter if it is confidential or not.
They should, at a minimum, have the ability to be remotely wiped.
They should be able to be tracked so we can find them.
They should have a lock screen that after a certain amount of minutes where the phone is not used, the screen locks.
And it should be set to if you enter the wrong password so many times the phone becomes a brick.
And if it is a company phone, we should also disable removable storage.
If we give our employees mobile devices and we are a small organization, it is possible we might just configure the phones by hand.
But as you know by now, anything that is done by hand is more susceptible to mistakes and omissions than anything that is automated.
This is the same reason we don’t harden our servers manually.
It should all be automated.
So when we start moving into the hundreds or thousands of devices, that automation should have it in a centralized system and that will be an MDM, a mobile device management system.
Using that, we can give every single phone a standard basic configuration that we know is secure.
And then on top of that, we can add to our group specific configurations.
So the server team might need access to certain things or the phone needs certain capabilities.
Well, then we add that to the server team profile.
We can also add application, white or black listing.
Here, white listing is preferred because white listing is us saying only these applications are allowed.
If you try to install anything that is not on that specific list, you can’t install it.
Whereas a blacklist is us listing all the applications we don’t want installed, which is almost impossible to keep up with.
I mean, there are thousands of new applications every day.
We can, also with MDMs, at storage segmentation, we can add or remove remote access, we can push new configuration out, take backups of the device and so much more.
Now, let’s say an employee leaves the company and they don’t bring their phone back.
Well, then we can either completely wipe it or we can just wipe the parts of the drive that we know contains company information.
It gives us that flexibility that we need to secure our company data.
And now a slightly controversial topic.
Since we monitor and manage their device, we can also see what traffic they use, where they are, which phone calls they make.
Now, that may or may not be legal where you live, if we as a company do that in any way, shape or form, they need to be told and they need to sign a form where they say, I agree to all of this before they get the device.
The MDMs can be an amazing tool, it can help us a lot.
But we need to make sure that what we do with it is also legal.
And the MDM is not just for smartphones.
It can easily track laptops, tablets and really anything that can be managed and tracked in a centralized system.
Laptops, smartphones, and tablets are amazing productivity tools.
I know that anywhere where I have worked, where we have had them, they certainly make my day and my work life much, much easier.
But as with anything else, they have to be secure the right way or they are a liability.
Which then brings us to BYOD.Bring your own device, which is super awesome if you are a user.
Maybe not so much if you are someone in security, now instead of having fifteen different devices that we hand out that we have configurations for, now, we may have hundreds or thousands of different devices that gets brought to work and used on our network.
So with BYOD, we should have a clear policy, when they bring their own devices to work.
We have a policy, we have procedures and we have guidelines on what is acceptable use and what is not.
They need to clearly understand how they are allowed to use their own devices.
And we also need to be very clear on how much support we offer for their own devices.
If we have, like I said, 10, 15 devices that we issue, well, then our help desk can easily keep up with that.
They can have the proper procedures in place.
But they most likely won’t have that for the hundreds of different devices our employees bring in.
And how we do that is really depending on our organization, what are we trying to do and what our capabilities.
It is that fine balance that we always need to strike between being user friendly while still having enough security.
Here, a possible solution could be that we add their personal devices to our MDM.
They accept that when they are on company property, we to some extent monitor what they do and cannot do.
So with the MDMs and mobile security, we have a lot of questions that we need to ask.
And then with those answers, we design our policies, our procedures, and our guidelines.
If we give them mobile devices, how do we make sure we get them back when they’re terminated or leave the company?
Or at least that we can wipe the device, if they use their own devices? How do we ensure there’s no company data left on it when they leave?
And how do we ensure that the sensitive data they have on their device is not accessible to anyone from the outside?
How do we ensure that they don’t go home and transfer that data to another device?
How do we make sure they have the latest patches, the latest antivirus and on and on.
Before we add any mobile devices to our networks or allow our employees to bring their own devices?
There’s a lot of thoughts and considerations we have to go through to make sure that the implementation we choose is both secure enough while still allowing our employees to do what they need to do in the easiest possible way.
And with that, we are done with this lecture.
I will see you in the next one.
CISSP Tips and Tricks | How to build your CISSP study plan
Having the right approach, the right materials and using the materials at the right time in your CISSP studying is critical for passing your CISSP exam.
Learn how to build your own CISSP study plan, how to manage your study time right, and what to study in which order.
Get my free CISSP study course to get the full free CISSP: How to study course, it also has the fillable study plans for you to use. https://thorteaches.com/get
https://youtu.be/hVI-0T9OvUk
You can get all my courses, free study materials, my free CISSP course and much more on https://thorteaches.com/
Transcript:
In this lecture, we’re going to talk about study plans, how to get them, how to tailor them to your specific needs and how to use them in your studying.
And to begin, I’m going to answer a question I get asked multiple times a week, how long should I study?
And every time I get the same answer, I have no clue.
I have had students who studied for one week and passed their exam and I have had others that been over a year.
Normal is somewhere between four to six months, and it varies so much because everybody comes into the CISSP studying from a different point of view.
You have a different background, you have different knowledge, people are different in how fast they learn.
How much time they spent every day studying, how focused they are, and 50 other things that will influence how long you need to study to pass your exam.
So in this lecture, I’m going to approach it with a normal student in mind that uses the four to six months.
For something as big and as complex as the CISSP, I suggest you study at least two to three hours every day, and when I say every day, I actually mean it.
It is every day.
And many of my students say, “Well, I can’t just find two hours in the day or three.
I can’t make more hours in the day than there are.”
Completely true.
What you need to do is do less of other things and you need to find those little pockets of time where you have 10, 15, 20 minutes where you’re not doing something else, your commute, your breaks, your lunch break, all of that I use for studying.
I also take a close look at what else I do that is not urgent or important.
So I spend less time on Facebook or social media.
I watch less TV, I play less games, and try to do it in a way that doesn’t ostracize your friends and family but you still get the study time that you need to pass your exam.
And before we start looking at the actual plan, remember, the study plan is a living document.
If for some reason last week you did not have time to study enough or you all of a sudden had extra time, well, then you adjust the plan.
And now for the actual study plan, download the attached study plan from this lecture or go to thorteaches.com/study/ and then click on free stuff.
The first thing at the top on the free stuff is the study plan.
On the front page of the study plan, I have my suggestion on how you should approach your studying and which order you should do it in.
First off, get one to three video resources, watch them all and then take notes.
In my video courses, I have study guides you can use and then add your notes alongside those.
Once you have watched all the videos, then you read your primary book, you supplement your notes, then I suggest you read the Memory Palace, the CISSP Process Guide, the Sunflower Notes and the NIST documents.
And the NIST documents, you can find the same place that you do the study guide, thorteaches.com/study/ and then click on the free stuff.
Then you re-watch all the videos again, maybe at 1.5 or two times speed, you update your notes and after you have watched the videos the second time, either reread the book or just skim the highlights, the areas you’re not completely sure on or start doing practice questions.
Practice questions is where you are going to spend maybe 50% of your study time.
Do a practice test mark everything you’re not completely sure on for review, once the test is over and you get the results, everything you had marked for review or that you got wrong, you go, restudy those topics, read the book, watch the videos, do online research, look in the study guides, and then you do another practice test.
And that is really what you’re going to do for the rest of your studying.
Plus some reviews every so often, use the easy to mid questions first, fifteen hundred to thirty five hundred of those and then the hard questions towards the end of your studying and you have probably heard me say before, do not reuse practice questions.
First off, if you have already used those questions, then you have already found the weak areas that you have that they could show you.
Second off, next time you reuse those questions, you’re going to remember some of the answers, meaning if you took it the first time, maybe you scored 70%.
When you take it the second time, maybe you score 85.
But that 85% is not really a true representation of where you are as far as being ready.
And now that we have all the practical stuff out of the way, let’s look at the actual study plan.
So my template study plan here is based on two hours every day, seven days a week.
If you can use more time, wonderful.
And of course, I use my resources, the ones that I recommend in this study plan, if you’re using something else, well just replace it with that.
And the last page in this study plan is a blank page.
It has the days.
It has the weeks, but it has nothing filled in, meaning you can fill it in with whatever you are using.
So the first two days I have, make your own study plan and watch the Thorteaches.com CISSP Intro course.
The Intro course has no set curriculum, but it has all the practical stuff.
How you should study, how you can be better prepared, how you should approach videos, books, questions, and everything else.
So you make sure that you study as efficiently as possible.
Then for the rest of the first four weeks, you watch two hours of my videos and the secondary videos you have chosen every day and you take notes.
Most students that I have talked to download my study guide and then alongside that they add their own notes.
And if you are a student on Thorteaches.com, one of the first lectures of the video course will have all the study guides for all eight domains.
If you are a student on Udemy, it is attached to the first lecture of each domain.
So that is all the time if you use two hours a day for four weeks.
Then we’ll go to week five.
Here, you read your primary book and as you can see, I have selected 50 pages a day.
Plus, take your own notes.
Some students might be able to read more, some less.
Adjust it to fit what you do.
And remember, it’s not just read the book.
It is read it, understand it, and be able to explain it.
I have had students who told me, “But Thor, I did what you said.
I read the whole book twice.
I did 5,000 questions and I didn’t pass.”
But then when I start talking to them about the concepts, they have no clue.
They just read as fast as they could through the entire book, not remembering anything.
And they did the same with the questions.
They just did a test.
Oh, I scored 65%, and then they moved on.
They never looked at all the things they had wrong.
And since they never looked at all the things they had wrong, they never improved their knowledge.
So it is not just read the book, it is read the book, take notes, understand the topics and be able to explain them.
Reading your primary book continues all the way into the middle of week eight, at this point, start reviewing your notes.
I have set aside four days for that use, more or less, depending on what you want, but be able to explain all the concepts and for each concept, be able to explain what it is, where we would use it, when we would use it, why we would use it, and how we would use it.
After those four days of review, I suggest you read the Sunflower Notes, the Memory Palace, CISSP Process guides and all the relevant NIST documents.
For this, I have a lot of six hours.
After those, you have two weeks of review, review the videos, watch them at 1.5 or two times speed, supplement you notes where you’re lacking, then reread or reskim the book, again at your notes and then another review session.
Two days where you explain why, where, when, how, what.
At this point, you’re about halfway in your studying.
From here on out, it is practice questions.
For the first week, I have set you to do between 50 and 100 questions every day.
After the first week, I dial that up to 100 to 150.
So every day you do one full practice test between 100 and 150 questions, once you are done, you review everything you marked for review and you review everything you got wrong.
Restudy those areas and then the next day you do another test.
For some students, there’s just not enough time to do 100 or 150 questions and then review them in two hours.
Well, then one day you do the test, the next day you review everything and restudy.
If you look here at week 13 to 16, you can see everything is practice questions that continues all the way into week 17.
Now at this point, if you are not consistently scoring 80% plus on the mid to easy tests or at least 70-75% on the hard ones, then do more questions.
If you are scoring in those areas, well then it is time to review, review your study notes, the PDFs, the videos and the areas of the book you had issues with and do that for three days.
Then re-watch all the thorteaches.com videos, here watch it as fast as you can.
Most students can do this at at least 1.5 or two.
When you’re done with this, we’re in week 19, here, I suggest you read the 11th Hour, Luke Ahmed’s and Wentz Wu’s books and then research online for any topics that you’re not completely clear on.
We have six days or 12 hours allotted to that, after that, reread the Sunflower Notes, the Memory Palace, the CISSP Process guides and the NIST documents, and pretty much do this until you’re ready for the exam.
After reviewing everything, I have some students that go back and take two or three days of practice questions just to get back in the practice question mindset.
And I also have some that on exam day right before going into the exam, do 10, maybe 20 questions.
Not enough to wear your brain out, but enough to get yourself back into the question mindset.
They should take you all the way to exam day.
Remember to adjust the plan as things change.
It is a living document and good luck on your exam.
And with that, we’re done with this lecture.
I will see you in the next one.
Updates we are working on 💻 🗓️
- A course on using generative AI for Project Management.
Updates we have completed 🍾 🎯
Video and test courses updates:
Our CISSP course is updated for the 2024 exam changes – Get it here.
Our FREE “CISSP: How to study course” – Get it here.
Our CC (Certified in Cybersecurity) course was updated in 2022, 2023, and will get more updates in 2024 – Get it here.
Our CISM course was updated in 2022, 2023, and we plan 2024 updates – Get it here.
All courses:
We have added subtitles in English, Spanish (Latin America), French, Arabic, Chinese, and Hindi to all our CISSP, CISM, and CC courses.
Practice question updates:
CC (Certified in Cybersecurity): Get them here
Added 1,700 new questions.
CISSP: Get them here
Added 3,250 new Easy/Mid CISSP questions – both as exam emulation and per-domain tests.
Added 125 new Hard CISSP questions.
Added 198 new CISSP topic quizzes added to our CISSP videos after each major topic.
Other:
150+ student names added to our practice questions, we want you to be part of our questions.
Glossary updates:
Our FREE 2,500 word IT and Cybersecurity Glossary – CISSP, CISM, CC, CCSP:
https://thorteaches.com/glossary/
ThorBots (Chatbots) updates:
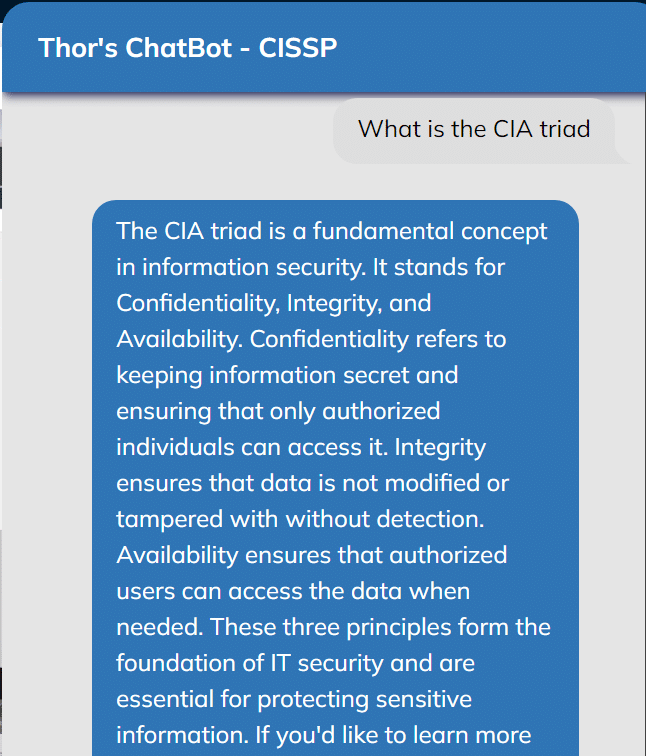
ThorBot:
Your 24/7 AI study assistant, clarify concepts, tailor your learning, and enhance your CISSP, CISM, and CC preparation. The ThorBots are included in our CISSP, CISM, and CC courses here on ThorTeaches.com
Indexes for acceability updates:
Added page indexes to all our Study Guides and Quick Sheets for better accessibility and navigation.
The NEW Thor's CISSP Quick Sheets:

Introducing the NEW “Thor’s CISSP Quick Sheets”.
Streamline your review sessions, maximize your retention!
We know you're busy, and that's why we've distilled our comprehensive CISSP Study Guides down to the essentials.
ThorTeaches.com proudly presents our new CISSP Quick Sheets – the ultimate condensed study notes tailored for your review sessions.
We have already added the CISSP Quick Sheets to our courses on Udemy and ThorTeaches.com, there is no additional charge or price increase, just another awesome study resource to help you succeed.
You can download them from the resources section in the first or second lecture of the course.
Our Flashcards on ThorTeaches.com are LIVE!
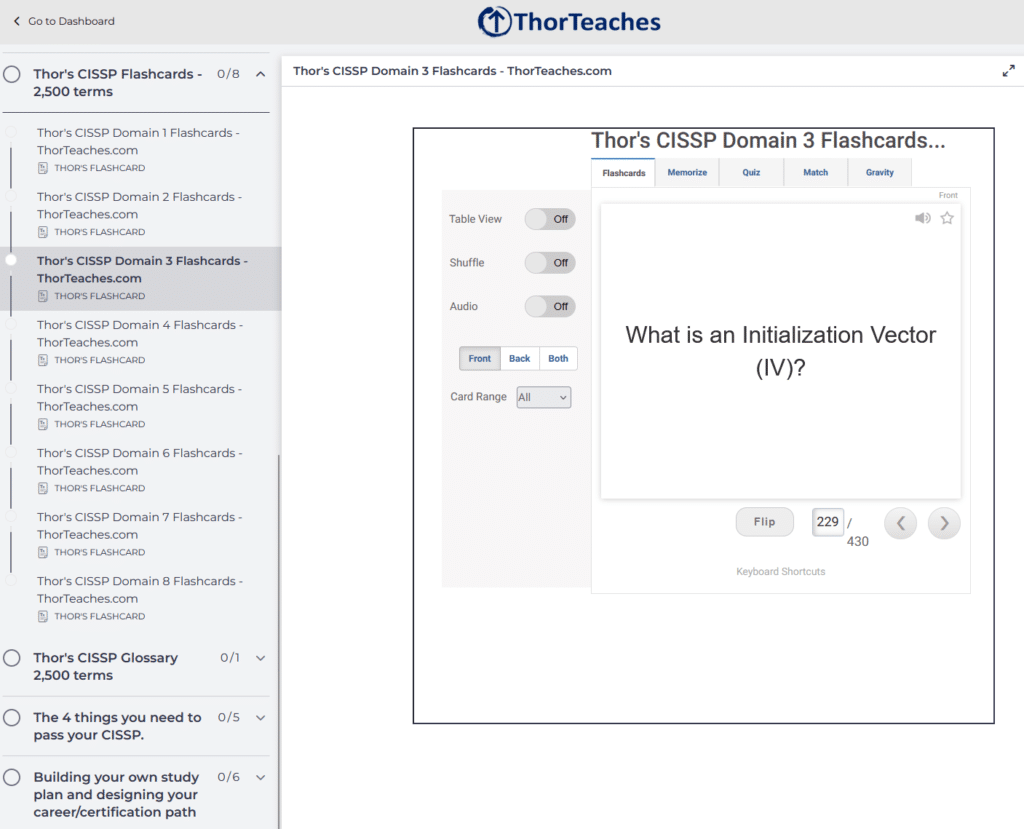
After many many months of working, our 2,500 CISSP, CISM, and CC Flashcards are finally here for you to use.
They are separated into primary domains for each certification as the perfect study aide for self-testing, review sessions, and reinforcing the material covered in our courses.
Where can I get the Flashcards?
They are ONLY available for our students with our CISSP, CISM, and CC courses on ThorTeaches.com, they are not available for Udemy students (sorry but it is an Udemy platform limitation).
Do they cost extra or will you raise your prices?
No, they are part of our full bundles. They were added to all our ThorTeaches.com CISSP, CISM, and CC students courses (right after the domain videos and the Glossary).
Can I use them on mobile devices too?
Yes, they are also accessible on your phone or tablet.
Can I download the flashcards?
No, they are only available on ThorTeaches.com in the courses.
Our CISSP is updated for 2024 exam changes – Get it here.
Our FREE “CISSP: How to study course” – Get it here.
Our CC 2022 (Certified in Cybersecurity) course – Get it here.
Our CISM 2022 curriculum updates – Get it here. <- next update is in 2027
All courses:
Added subtitles in English, Spanish (Latin America), French, Arabic, Chinese, and Hindi to all our CISSP, CISM, and CC courses.
Practice question updates:
CC (Certified in Cybersecurity): Get them here
Added 1,700 new questions.
CISSP: Get them here
Added 3,250 new Easy/Mid CISSP questions – both as exam emulation and per-domain tests.
Added 125 new Hard CISSP questions.
Added 198 new CISSP topic quizzes added to our CISSP videos after each major topic.
Other:
150+ student names added to our practice questions, we want you to be part of our questions.
Yes, there will be detailed explanations of why the correct answer is correct and why the incorrect answers are incorrect.
Easy (E) level sample question:
Louise is the IT security manager for a large financial institution. She has recently implemented a new access control system that utilizes multi-factor authentication for all employees to access sensitive data. One of her employees, Hanna, has reported that she is unable to access certain data that she should have access to. After investigating the issue, Louise discovered that Hanna's access privileges were inadvertently revoked by another employee. What is the most appropriate action to take in this situation?
- Reassign Hanna's access privileges to the appropriate level.
- Have Hanna go through the multi-factor authentication process again to verify her identity.
- Have Hanna go through the entire onboarding process again, including security training and background checks.
- Terminate Hanna's employment for security breaches.
The correct answer:
Reassign Hanna's access privileges to the appropriate level: This is the most reasonable and efficient solution. The issue at hand is that Hanna's access privileges were mistakenly revoked. The most direct way to resolve the problem is to reassign these privileges at the level that is appropriate for her role. This should allow Hanna to access the data she needs for his work. We might also want to investigate how it happened to see if we want to implement further checks to avoid this in the future.
The incorrect answers:
Have Hanna go through the multi-factor authentication process again to verify her identity: The issue isn't with Hanna's identity verification but rather with her access privileges. Re-doing the multi-factor authentication won't restore access to the resources she needs.
Have Hanna go through the entire onboarding process again, including security training and background checks. This approach is unnecessary and time-consuming. The issue doesn't stem from Hanna's actions or a lack of training. It's a mistake in the access control settings. Also, making an employee repeat the onboarding process because of a simple administrative error could lead to frustration and lower morale.
Terminate Hanna's employment for security breaches: This is inappropriate because Hanna didn't commit any security breaches. In fact, she reported the problem. Her access was revoked due to an internal administrative error, not because of her own actions. Taking such a drastic step as termination would not only be unjust, but it could also create a hostile environment where employees may be afraid to report problems in the future.
All of them will be on ThorTeaches.com; most will be on Udemy.
CC Udemy has 1,200 CC questions, ThorTeaches.com has all 1,700 questions.
The CISSP courses on Udemy has 2,500 Easy/Mid questions as exam emulation and 1,000 as per-domain questions.
ThorTeaches.com has 3,250 Easy/Mid questions as exam emulation and 3,250 as per-domain questions.
Both have 625 HARD CISSP questions.
For UB (Udemy Business) students, you should have access to the new Udemy tests as soon as they are added to UB.
All the E/M tests are being retired and replaced with newer and better tests. all this is done in place, so your courses get updated for free. Hard questions are being added to.
On Udemy, we are updating questions in the current tests. We are also making new courses on Udemy for all the other questions.
On ThorTeaches.com, we are adding all the new questions to the bundles there; if you are a current subscriber, you get them all for free.
We plan to raise our prices to match all the new content, but we will announce a 1-week period where you can buy the bundle at the old price but still get all the new questions for free.
They will be better formulated with much better explanations. The test interface stays the same on Udemy and ThorTeaches.com.
Yes, all questions are based on the current CC (2023), CISSP (2021), and CCSP (2022) exams, and they will be updated when the exams change again.
The CISSP exam, will update April 15th. 2024, CCSP 2025, CC 2026, and CISM 2027. Questions will be updated at that time.
It's the same place you do now; we are just updating the back-end practice tests.
A ton of student requests, “Why don’t you have more questions?”, “Can you make more questions, please?”, “I really want just to use your questions,” and many more.
You ask, I listen 😊
Yes, please! With that many new questions, your feedback is invaluable to us.
Aamir, Abhishek, Abiola, Abwino, Adeel, Adu, Ala, Alamgeer, Alfred, Alpesh, Alvin, Amolak, André, Andreas, Ashish, Ashlyn, Brent, Chinthake, Chirayu, Claire, Daniel, Debashish, Dhievy, Donita, Edward, Emmanuelle, Erin, Esther, Evan, Fahim, Garry, Gireesha, Guru, Gurudev, Habib, Hannah, Hind, Hrishikesh, Ishara, Ismail, Ivan, Ivy, Jacob, Jai, Javed, Jay, Jeyapaul, Joe, Joy, Joye, KaTina, Kazim., Khoa, Kobamelo, Kojo, Krzysztof, Kundai, Kushal, Leny, Livaniel, Liz, Malini, Marc, Marius, Maston, Melissa, Mervin, Michael, Moshood, Moxi, Nader, Neeraj, Newton, Olatunde, Omar, Philip, Pierre, Prasanth, Raghavendran, Rami, Ravi, Ritesh, Riz, Robert, Rogelio, Rohit, Ron, Ryan, Saad, Saeed, Sajeevkumar, Sameer, Sartsatat, Serena, Seth, Stuart, Syed, Tai, Taye, Terence, Tewfik, Thilina, Travis, Tristan, Tunde, Vihanga, Vikas, Vinit, Yokesh, Zaw, Scott, Jason, Prashant, Marteen, Fadi, Luc, Shon, Ku'uipo, Chris, Kaimana, Sara, Yasmine, Maria, Melissa, Fatma, Fatima, Nora, Mariam, Emma, Olivia, Isabella, Victoria, Ana Maria, Carmen, Helena, Manuela, Guadalupe, Malu, Esther, Kyra, Sofía, Luna, Zahra, Himari, Latifa, Shu-fen, Amelia, Freja, Agnes, Lív, Ronja, Louise, Hanna, Kamilė, Zuzanna, Anastasia, Astrid, Amelia, Leilani, Kalea, Makana, Kamalani, Francesca, Juanita, Prabh, Ana,Henry, Mikey, Syed, Ushakiran, Sanjay, Paskorn, Suobo, Darwin, Adeel, Jose
Our FREE 2,500 word IT and Cybersecurity Glossary – CISSP, CISM, CC, CCSP: https://thorteaches.com/glossary/
Our Flashcards on ThorTeaches.com are LIVE!
After many many months of working, our 2,500 CISSP, CISM, and CC Flashcards are finally here for you to use.
They are separated into primary domains for each certification as the perfect study aide for self-testing, review sessions, and reinforcing the material covered in our courses.
Where can I get the Flashcards?
They are ONLY available for our students with our CISSP, CISM, and CC courses on ThorTeaches.com, they are not available for Udemy students (sorry but it is an Udemy platform limitation).
Do they cost extra or will you raise your prices?
No, they are part of our full bundles. They were added to all our ThorTeaches.com CISSP, CISM, and CC students courses (right after the domain videos and the Glossary).
Can I use them on mobile devices too?
Yes, they are also accessible on your phone or tablet.
Can I download the flashcards?
No, they are only available on ThorTeaches.com in the courses.

ThorBot:
Your 24/7 AI study assistant, clarify concepts, tailor your learning, and enhance your CISSP, CISM, and CC preparation.
The ThorBots are included in our CISSP, CISM, and CC courses here on ThorTeaches.com.
Updated again Feb 2024 with better back-end (ChatGPT 4-Turbo 128 and better command training.

Added page indexes to all our Study Guides and Quick Sheets for better accessibility and navigation.

Introducing the NEW “Thor’s CISSP Quick Sheets”.
Streamline your review sessions, maximize your retention!
We know you're busy, and that's why we've distilled our comprehensive CISSP Study Guides down to the essentials.
ThorTeaches.com proudly presents our new CISSP Quick Sheets – the ultimate condensed study notes tailored for your review sessions.
We have already added the CISSP Quick Sheets to our courses on Udemy and ThorTeaches.com, there is no additional charge or price increase, just another awesome study resource to help you succeed.
You can download them from the resources section in the first or second lecture of the course.
What are the main practical changes in the CISSP 2024 exam update?
My video on the changes:
https://www.youtube.com/watch?v=nFd0TQ5oBT8
The CISSP 2024 exam update, includes a 1% weight shift from Domain 8 to Domain 1, fewer exam questions (100 to 150 instead of 125 to 175), and a shorter exam duration (3 hours instead of 4). Additionally, there’s an update in curriculum content across various domains, including new and expanded topics.
What are the actual curriculum changes?
Most of the changes is more emphasis on topics that are more relevant and in focus now like cloud computing, AI, privacy, etc.
Domain 1: Added external dependencies in business impact analysis.
Domain 2: No changes we know of.
Domain 3: Added Secure Access Service Edge (SASE), Quantum key distribution, and managing the information system lifecycle.
Domain 4: Added transport architecture, performance metrics, traffic flows, physical segmentations, edge networks, virtual private clouds, and network monitoring and management.
Domain 5: Added services in the control of physical and logical access to assets, policy decision and enforcement points, and service account management.
Domain 6: Emphasis on location context (on-premise, cloud, hybrid) for audit strategies.
Domain 7: Added communication during the testing of Disaster Recovery Plans (DRP).
Domain 8: Added Scaled Agile Framework and software composition analysis.
When will your new content be out for the CISSP changes?
Content for 2024 curriculum changes is now live .
Is anything of the current curriculum getting removed?
We do not think so, as far as we know no curriculum is being removed.
Will there be any new domains introduced in the updated CISSP exam?
No, the eight domains will remain the same; only the content within some domains will be updated or expanded.
How will the question format be affected by the update?
The question format will remain a Computer Adaptive Testing (CAT) format, but with a different number of questions and reduced exam duration.
If I’m already studying, should I attempt the exam before or after the update?
It is generally recommended to take the exam before the update, given that the current materials are available, and you might be more familiar with them. However, if that’s not possible, the changes are considered minor and should not significantly impact your preparation.
Will I need to repurchase your study courses for the updated exam if I already have them?
No, if you have purchased courses from ThorTeaches.com or Udemy, you will receive updates for free. Only the versions on these platforms will be updated.
Can I take the CISSP exam remotely after the update?
No, all exams must be taken in-person at an authorized Pearson-Vue testing center.
What happens if I have already purchased study materials for the current exam but plan to take it after the update?
You should be fine, the changes are very minor. It is advisable to review the new topics from other sources as the update will introduce new content.
When will the new study materials for the 2024 exam changes be available?
For ThorTeaches.com and Udemy courses, updates will be made available before the exam changes. The official study guides, AIO, and practice questions from ISC2 typically become available 3 to 6 months after the exam updates.
Is there going to be a price change for the CISSP exam after the update?
There are no planned changes to the exam pricing.
How can I best prepare for the CISSP exam with the upcoming changes?
It is recommended to continue studying the current materials and familiarize yourself with the new topics. Taking advantage of the free course on how to study for the exam at free.thorteaches.com can provide valuable insights into effective preparation strategies.
Will the format of questions change in the updated CISSP exam?
The format will remain Computer Adaptive Testing (CAT), but there will be a total of 100 to 150 questions instead of the previous range of 125 to 175.
I am scheduled to take the CISSP exam right before the update; will my exam still be valid?
Yes, your exam and assuming you pass and get endorsed, your CISSP certification will be just as valid regardless of whether you take the exam before or after the update.
How much time will I have per question in the updated exam?
If you receive the maximum of 150 questions in your exam, you will have approximately 72 seconds per question within the 3-hour time limit.
What is the passing score for the updated CISSP exam?
The passing score for the CISSP exam remains the same, which is a scaled score of 700 out of 1000 points.
Will there be any changes to the CISSP experience requirements after the update?
There have been no announcements regarding changes to the CISSP experience requirements, which currently entail a minimum of five years of professional security work experience.
Do the CISSP exam updates include changes to the continuing professional education (CPE) requirements?
There are no changes to the CPE requirements for maintaining your CISSP certification.
Will beta questions be included in the updated CISSP exam?
Yes, there will be 25 beta questions randomly dispersed within the first 100 questions of the exam.
Are the beta questions counted towards the final score?
No, beta questions are not counted toward your final score. They are used by ISC2 to validate the questions for future exams.
Will the beta questions be distinguishable from the scored questions?
No, you will not be able to distinguish beta questions from scored questions during the exam.
Can we expect new types of interactive questions in the updated CISSP exam?
There is no specific mention of new question types; the update focuses on content rather than question format.
How will the changes affect the weight of each domain in the CISSP exam?
All domains except for Domain 1 and Domain 8 will maintain their current weights. Domain 1 will increase by 1%, compensated for by a 1% decrease in Domain 8.
Will the difficulty level of the CISSP exam change after the update?
The difficulty is calibrated through the CAT format to reflect a consistent standard of knowledge, so it should remain comparable.
How frequently are the CISSP exam questions updated?
While there is a major curriculum update every three years, the actual exam questions can be updated more frequently to reflect current industry standards and practices.
Will the update affect the application process for the CISSP exam?
The application process for the CISSP exam is not expected to change with the update.
Are there any changes to the CISSP endorsement process after passing the exam?
No changes to the endorsement process have been announced.
Why is Lifetime Access more expensive than the standard 12-month access?
The premium price of Lifetime Access accounts for the ongoing costs to maintain, host, and update the course materials on our platform indefinitely, rather than just for 12 months.
Do I get access to all your courses on ThorTeaches.com when I buy lifetime access?
No, the lifetime access is purchased on a course level. If you want lifetime access to more courses, you need to purchase the courses you want.
Can I upgrade to Lifetime Access on courses I have not purchased?
You can only upgrade courses you own to lifetime access, or you can buy them initially with Lifetime Access.
Will I receive updates to the course with Lifetime Access?
Yes, all in-place updates to the course content are included with Lifetime Access. You’ll automatically receive the most current material without additional charges.
What does Lifetime mean on ThorTeaches.com?
In the context of this policy, “Lifetime” refers to the operational lifetime of the course on our platform, not the lifetime of the individual purchaser. Should ThorTeaches LLC undergo a business transition, such as cessation, sale, or restructuring, you will be provided a download link for the full course and all materials that you are enrolled in, preserving your educational investment. There are no near or long term plans for this, but proper contingencies should be clear.
Are there any maintenance or hidden fees associated with Lifetime Access?
No, there are no maintenance or hidden fees. The one-time premium payment covers all costs associated with the lifetime access to the course materials.
Can I switch from a 12-month access plan to Lifetime Access after my initial purchase?
Yes, you can upgrade to Lifetime Access at any time during your 12-month access period or after it expires. There is no deadline, even if your initial access has expired you can still get lifetime for 45% of the current course list price. It’s more cost-effective to select Lifetime Access at the time of your initial purchase.
Is Lifetime Access transferable to another student or individual?
No, Lifetime Access is non-transferable and is linked exclusively to the account of the original purchaser to ensure the integrity and security of account access.
Does Lifetime Access apply to all courses offered on ThorTeaches.com?
Yes, it is available for all our courses.
Will I still be able to access the course after I finish it?
Absolutely. Once you’ve finish the course, you will retain access to it for as long as your account remains in good standing. That means you can revisit and review the course content whenever you need a refresher or want to retake the entire course.
How often is the course content updated?
We update courses to align with the current exam version, all updates are done in-place. With Lifetime Access, you’re guaranteed to receive all these updates.
Can I get Lifetime Access for the Boson questions?
No, the Lifetime Access is only for our courses, we resell the Boson vouchers, so they are only 12-months access.
Yes, there will be detailed explanations of why the correct answer is correct and why the incorrect answers are incorrect.
Easy (E) level sample question:
Louise is the IT security manager for a large financial institution. She has recently implemented a new access control system that utilizes multi-factor authentication for all employees to access sensitive data. One of her employees, Hanna, has reported that she is unable to access certain data that she should have access to. After investigating the issue, Louise discovered that Hanna's access privileges were inadvertently revoked by another employee. What is the most appropriate action to take in this situation?
- Reassign Hanna's access privileges to the appropriate level.
- Have Hanna go through the multi-factor authentication process again to verify her identity.
- Have Hanna go through the entire onboarding process again, including security training and background checks.
- Terminate Hanna's employment for security breaches.
The correct answer:
Reassign Hanna's access privileges to the appropriate level: This is the most reasonable and efficient solution. The issue at hand is that Hanna's access privileges were mistakenly revoked. The most direct way to resolve the problem is to reassign these privileges at the level that is appropriate for her role. This should allow Hanna to access the data she needs for his work. We might also want to investigate how it happened to see if we want to implement further checks to avoid this in the future.
The incorrect answers:
Have Hanna go through the multi-factor authentication process again to verify her identity: The issue isn't with Hanna's identity verification but rather with her access privileges. Re-doing the multi-factor authentication won't restore access to the resources she needs.
Have Hanna go through the entire onboarding process again, including security training and background checks. This approach is unnecessary and time-consuming. The issue doesn't stem from Hanna's actions or a lack of training. It's a mistake in the access control settings. Also, making an employee repeat the onboarding process because of a simple administrative error could lead to frustration and lower morale.
Terminate Hanna's employment for security breaches: This is inappropriate because Hanna didn't commit any security breaches. In fact, she reported the problem. Her access was revoked due to an internal administrative error, not because of her own actions. Taking such a drastic step as termination would not only be unjust, but it could also create a hostile environment where employees may be afraid to report problems in the future.
All of them will be on ThorTeaches.com; most will be on Udemy.
CC Udemy has 1,200 CC questions, ThorTeaches.com has all 1,700 questions.
The CISSP courses on Udemy has 2,500 Easy/Mid questions as exam emulation and 1,000 as per-domain questions.
ThorTeaches.com has 3,250 Easy/Mid questions as exam emulation and 3,250 as per-domain questions.
Both have 625 HARD CISSP questions.
For UB (Udemy Business) students, you should have access to the new Udemy tests as soon as they are added to UB.
All the E/M tests are being retired and replaced with newer and better tests. all this is done in place, so your courses get updated for free. Hard questions are being added to.
On Udemy, we are updating questions in the current tests. We are also making new courses on Udemy for all the other questions.
On ThorTeaches.com, we are adding all the new questions to the bundles there; if you are a current subscriber, you get them all for free.
We plan to raise our prices to match all the new content, but we will announce a 1-week period where you can buy the bundle at the old price but still get all the new questions for free.
They will be better formulated with much better explanations. The test interface stays the same on Udemy and ThorTeaches.com.
Yes, all questions are based on the current CC (2023), CISSP (2024), and CCSP (2022) exams, and they will be updated when the exams change again.
The CISSP exam has been updated for 2024, and the CCSP exam will be updated in 2025, the CC exam in 2026, and the CISM exam in 2027. The questions for these exams will be updated at those respective times.
It's the same place you do now; we are just updating the back-end practice tests.
A ton of student requests, “Why don’t you have more questions?”, “Can you make more questions, please?”, “I really want just to use your questions,” and many more.
You ask, I listen 😊
Yes, please! With that many new questions, your feedback is invaluable to us.
Aamir, Abhishek, Abiola, Abwino, Adeel, Adu, Ala, Alamgeer, Alfred, Alpesh, Alvin, Amolak, André, Andreas, Ashish, Ashlyn, Brent, Chinthake, Chirayu, Claire, Daniel, Debashish, Dhievy, Donita, Edward, Emmanuelle, Erin, Esther, Evan, Fahim, Garry, Gireesha, Guru, Gurudev, Habib, Hannah, Hind, Hrishikesh, Ishara, Ismail, Ivan, Ivy, Jacob, Jai, Javed, Jay, Jeyapaul, Joe, Joy, Joye, KaTina, Kazim., Khoa, Kobamelo, Kojo, Krzysztof, Kundai, Kushal, Leny, Livaniel, Liz, Malini, Marc, Marius, Maston, Melissa, Mervin, Michael, Moshood, Moxi, Nader, Neeraj, Newton, Olatunde, Omar, Philip, Pierre, Prasanth, Raghavendran, Rami, Ravi, Ritesh, Riz, Robert, Rogelio, Rohit, Ron, Ryan, Saad, Saeed, Sajeevkumar, Sameer, Sartsatat, Serena, Seth, Stuart, Syed, Tai, Taye, Terence, Tewfik, Thilina, Travis, Tristan, Tunde, Vihanga, Vikas, Vinit, Yokesh, Zaw, Scott, Jason, Prashant, Marteen, Fadi, Luc, Shon, Ku'uipo, Chris, Kaimana, Sara, Yasmine, Maria, Melissa, Fatma, Fatima, Nora, Mariam, Emma, Olivia, Isabella, Victoria, Ana Maria, Carmen, Helena, Manuela, Guadalupe, Malu, Esther, Kyra, Sofía, Luna, Zahra, Himari, Latifa, Shu-fen, Amelia, Freja, Agnes, Lív, Ronja, Louise, Hanna, Kamilė, Zuzanna, Anastasia, Astrid, Amelia, Leilani, Kalea, Makana, Kamalani, Francesca, Juanita, Prabh, Ana,Henry, Mikey, Syed, Ushakiran, Sanjay, Paskorn, Suobo, Darwin, Adeel, Jose
Can I get CPEs/CEUs for finishing your courses?
Yes, when you finish our course you get a Certificate of completion worth 1 CPE per hour of video watched.
You can use them for CPEs with ISACA, CompTIA, ISC2, and many other certification providers.
- The CISSP course is 32 hours long, worth 32 CPEs.
- The CISM course is 32 hours long, worth 32 CPEs.
- The CC (Certified in Cybersecurity) course is 17 hours long, worth 17 CPEs.
What are the ThorTeaches Chatbots?
Our AI Chatbots are digital study assistants that support interactive learning, offer on-demand assistance, and provide smart study strategies for CISSP, CISM, and Certified in Cybersecurity (CC) certifications.
How do I access the chatbots?
The chatbots are available exclusively for ThorTeaches.com students. Just log in to your account, and you'll find them ready to assist you.
Can anyone use the chatbots?
While full access is reserved for our students, we offer a free version with limited features on our website for everyone to try.
What kind of materials are the chatbots trained on?
The chatbots are trained using our video courses, study guides, mnemonics, NIST documents, Wikipedia articles, ISC2 and ISACA websites, our own "How to Study" materials, and various study guides like The CISSP Process Guide, The Sunflower Notes, and The Memory Palace.
Can the chatbots help me understand complex topics?
Yes, you can ask them to explain complicated subjects in simpler terms to enhance your understanding.
Are the chatbots available 24/7?
Absolutely! Our chatbots are ready to provide assistance around the clock, any day of the week.
Will the chatbots provide personalized study tips?
They sure can. The chatbots will offer tailored advice based on our proven study methods and resources.
Can I rely on the chatbots for accurate information?
While the chatbots are trained to provide accurate information, please be aware that they may occasionally make errors. Always cross-reference with authoritative sources when in doubt.
Do the chatbots offer support for exam logistics and scheduling?
Yes, they can provide information on exam rules, registration, and scheduling processes.
What is the cost of using the chatbots?
The chatbots are included as part of the educational resources provided to students of ThorTeaches.com. The slimmed-down version on our website is free.
How do the chatbots handle copyrighted content?
Our chatbots are trained on non-copyrighted, copyright with attribution, or proprietary ThorTeaches materials.
Can the chatbots help with mnemonic devices?
Yes, they can teach you mnemonics to improve your memory of important concepts.
Can the chatbots help with mnemonic devices?
Yes, they can teach you mnemonics to improve your memory of important concepts.
Is there a limit to the number of questions I can ask the chatbots?
No, you can ask unlimited questions and engage with the chatbots as much as you need.
Are the chatbots updated regularly?
Yes, we ensure our chatbots are updated in line with the latest information and best practices.
Do the chatbots cover all domains of the certification exams?
Yes, they provide assistance across all domains covered in the CISSP, CISM, and CC exams.
Will the chatbots replace my need for traditional study methods?
No, they act as a complement to traditional methods by providing interactive and dynamic learning assistance.
Can the chatbots help me prioritize my study topics?
Yes, ask the chatbot for advice on which topics to focus on based on your knowledge gaps and exam weightings.